TrickGate, a packer used by malware to evade detection since 2016
Security Affairs
JANUARY 31, 2023
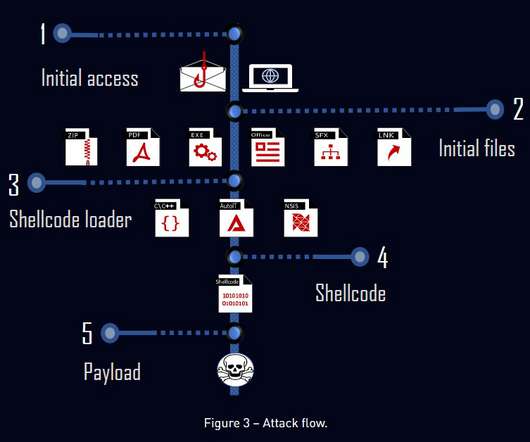
TrickGate is a shellcode-based packer offered as a service, which is used at least since July 2016, to hide malware from defense programs. The TrickGate packer was primarily used in attacks aimed at the manufacturing sector, and other attacks aimed at the education, healthcare, government, and finance industries.




















Let's personalize your content