Vladimir Putin ‘s computers still run Windows XP, Media reports
Security Affairs
DECEMBER 30, 2019
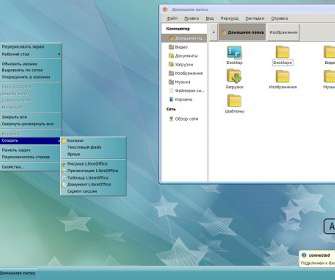
Astra Linux is a Debian-based distro developed in Russia by the Scientific/Manufacturing Enterprise Rusbitech RusBITech about ten years ago. The exercises aimed at testing and ensuring the integrity and the security of Russia’s Internet infrastructure, so-called RuNet. ” concludes The Guardian. Pierluigi Paganini.
















Let's personalize your content