Iran-linked group Cobalt Dickens hit over 60 universities worldwide
Security Affairs
SEPTEMBER 12, 2019
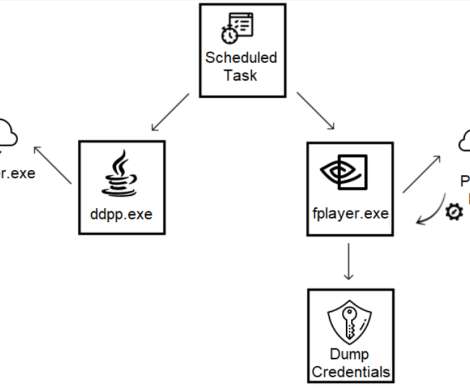
This operation is similar to the threat group’s August 2018 campaign , using compromised university resources to send library-themed phishing emails.” The hackers appear to be interested in getting access to the library, they sent phishing messages to people with access to the library of the targeted university.





















Let's personalize your content