OceanLotus APT group leverages a steganography-based loader to deliver backdoors
Security Affairs
APRIL 3, 2019
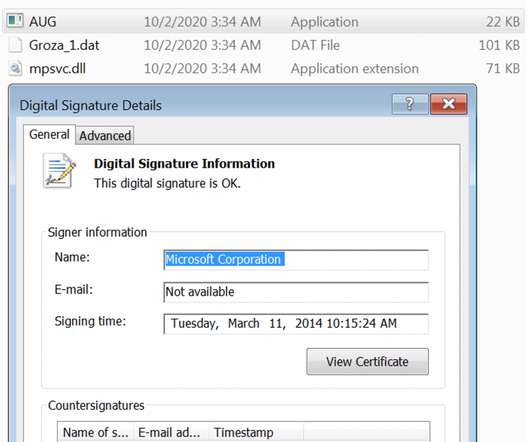
The APT32 group, also known as OceanLotus Group, has been active since at least 2013, according to the experts it is a state-sponsored hacking group. “ Threat actors used a custom steganography algorithm to hide the encrypted payload within PNG images to to avoid detection. ” reads the report published by the experts.























Let's personalize your content