Over 61% of Exchange servers vulnerable to CVE-2020-0688 attacks
Security Affairs
SEPTEMBER 30, 2020
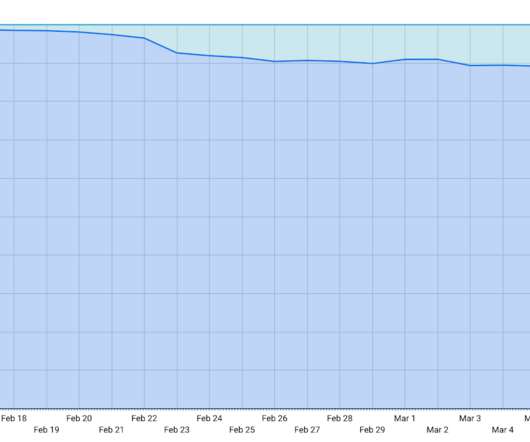
Security experts Simon Zuckerbraun from Zero Day Initiative published technical details on how to exploit the Microsoft Exchange CVE-2020-0688 along with a video PoC. Researchers from Rapid7 reported that 61 percent of Exchange 2010, 2013, 2016 and 2019 servers are still vulnerable to the vulnerability. Pierluigi Paganini.


























Let's personalize your content