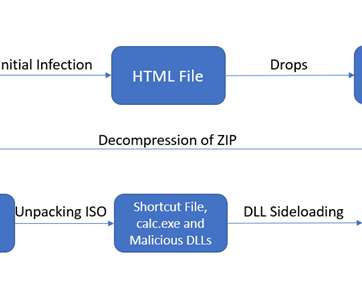
Threat actors leverages DLL-SideLoading to spread Qakbot malware
Security Affairs
JULY 26, 2022
Dynamic-link library (DLL) side-loading is an attack method that takes advantage of how Microsoft Windows applications handle DLL files. Qakbot , also known as QBot, QuackBot and Pinkslipbot, is an info-stealing malware that has been active since 2008. ” reads the analysis published by Cyble.



















Let's personalize your content