PurpleFox botnet variant uses WebSockets for more secure C2 communication
Security Affairs
OCTOBER 20, 2021
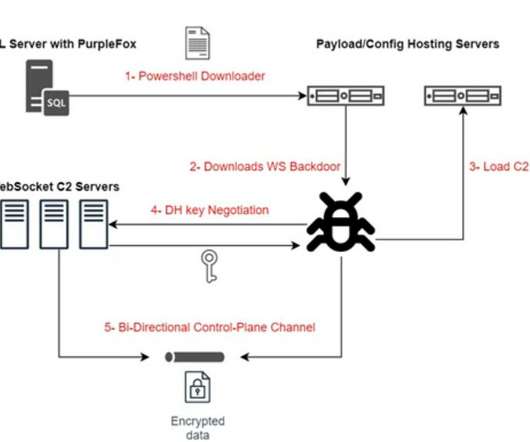
Its operators have added new exploits and payloads, according to the experts, the new variant leverages WebSockets to implement more secure C2 bidirectional communication. The analysis of the C2 infrastructure revealed that the most notable activity is in the US, Turkey, UAE, Iraq, and Saudi Arabia. ” continues the analysis.

























Let's personalize your content