New TunnelVision technique can bypass the VPN encapsulation
Security Affairs
MAY 8, 2024
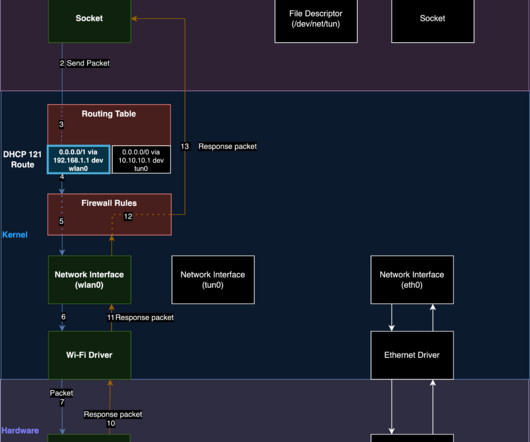
The technique causes the VPN to fail to encrypt certain packets, leaving the traffic vulnerable to snooping. TunnelVision exploits the vulnerability CVE-2024-3661, which is a DHCP design flaw where messages such as the classless static route (option 121) are not authenticated and for this reason can be manipulated by the attackers.



















Let's personalize your content