EvilProxy Phishing-As-A-Service With MFA Bypass Emerged In Dark Web
Security Affairs
SEPTEMBER 5, 2022
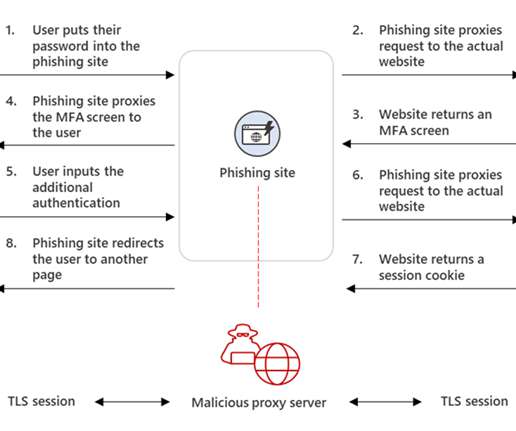
Based on the ongoing investigation surrounding the result of attacks against multiple employees from Fortune 500 companies, Resecurity was able to obtain substantial knowledge about EvilProxy including its structure, modules, functions, and the network infrastructure used to conduct malicious activity. How It Works? Google 2FA.











Let's personalize your content