Cybersecurity Trends to Watch in 2024
Data Breach Today
JANUARY 1, 2024
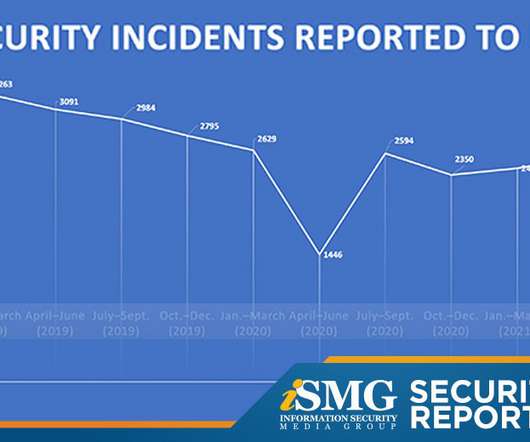
Expert Panelists Debate Impact of AI, Geopolitics and New Tactics in the Year Ahead In conjunction with a new report from CyberEd.io, Information Security Media Group asked some of the industry's leading cybersecurity and privacy experts about 10 top trends to watch in 2024.

















































Let's personalize your content