Embedded PLC Web Servers a Vector to New Class of OT Malware
Data Breach Today
MARCH 7, 2024
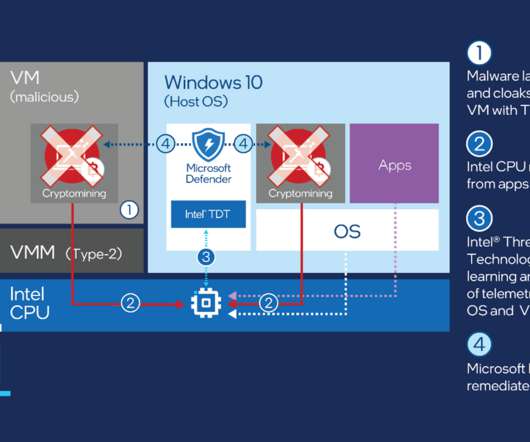
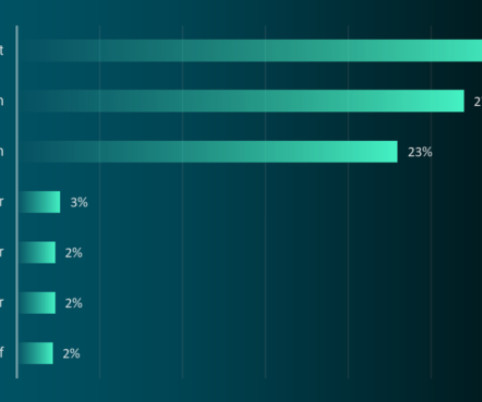
Web PLC Malware Holds Potential for Catastrophic Incidents Fusty and fussy operational technology devices are probably the farthest things away from a web server. But web servers embedded into industrial firmware are also a potential bonanza for hackers, say researchers from the Georgia Institute of Technology.





































Let's personalize your content