Russia Tops Global Cybercrime Index, New Study Reveals
Data Breach Today
APRIL 10, 2024
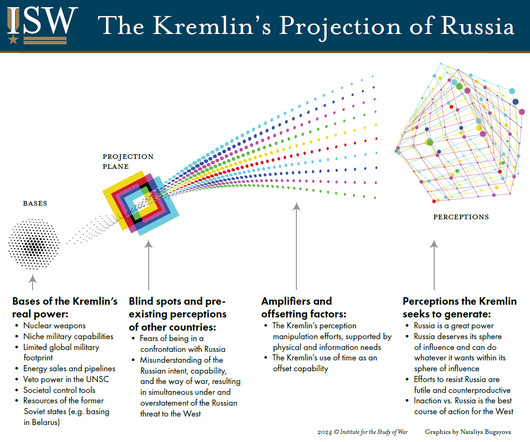
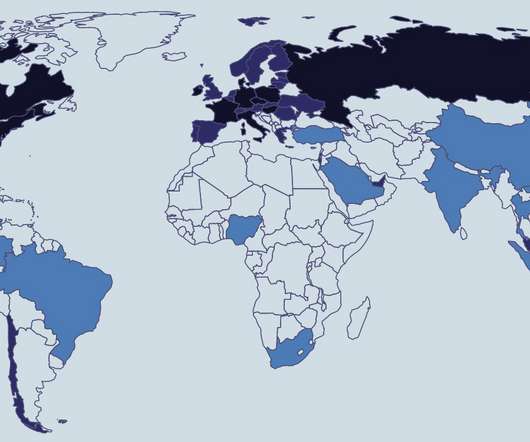
Russia, Ukraine, China and US All Top 'First-Ever World Cybercrime Index' A new study published by researchers from the universities of Oxford and New South Wales ranks Russia at the top of a global list of cybercrime hot spots and says Ukraine, China, the United States, Nigeria and Romania are home to a majority of global cybercriminal activity.






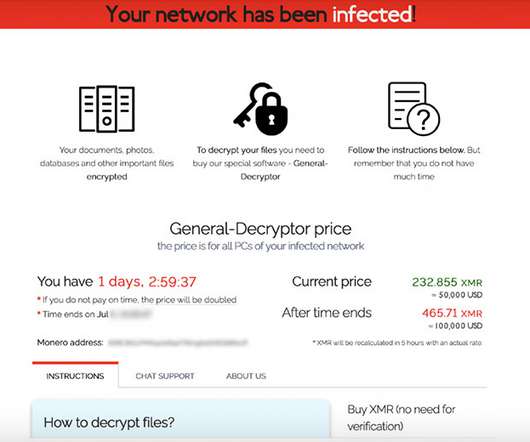








































Let's personalize your content