STEPS FORWARD Q&A: Will ‘proactive security’ engender a shift to risk-based network protection?
The Last Watchdog
OCTOBER 4, 2023
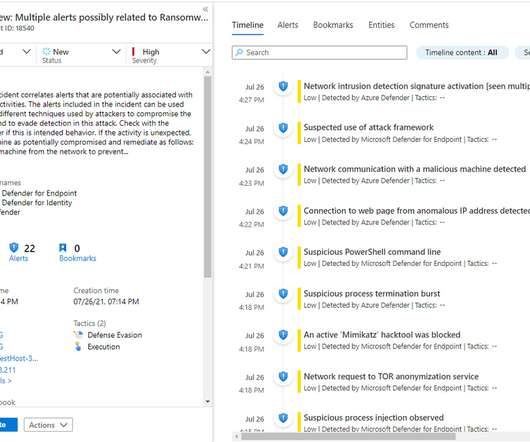
What I came away with is that many of the new cloud-centric security frameworks and tools fit as components of proactive security, while familiar legacy solutions, like firewalls and SIEMs, can be categorized as either preventative or reactive security. This is a useful way to look at it. Is that fair?

















































Let's personalize your content