Malicious app exploiting CVE-2019-2215 zero-day available in Google Play since March
Security Affairs
JANUARY 7, 2020
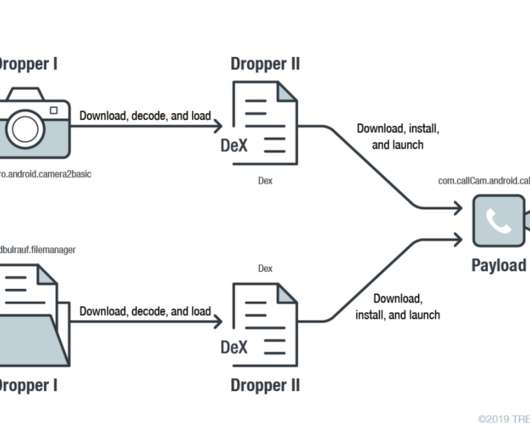
Security experts have found a malicious app in the Google Play that exploits the recently patched CVE-2019-2215 zero-day vulnerability. Earlier October, Google Project Zero researchers Maddie Stone publicly disclosed a zero-day vulnerability , tracked as CVE-2019-2215 , in Android. ” reads a blog post published by Stone.


















Let's personalize your content