OpenAI and Microsoft Terminate State-Backed Hacker Accounts
Data Breach Today
FEBRUARY 15, 2024
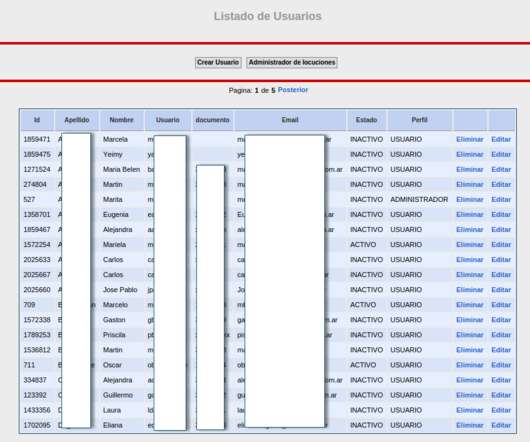
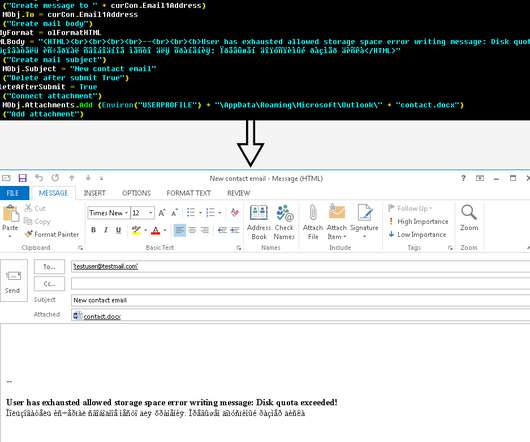
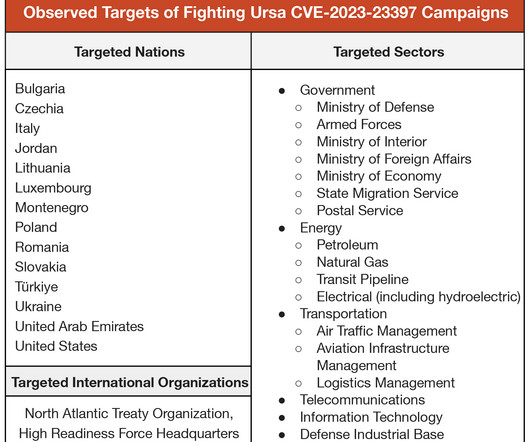
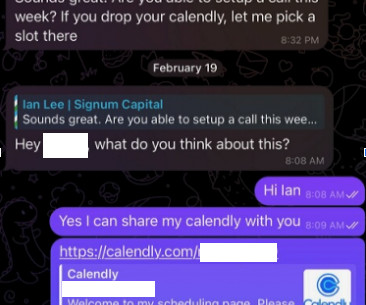
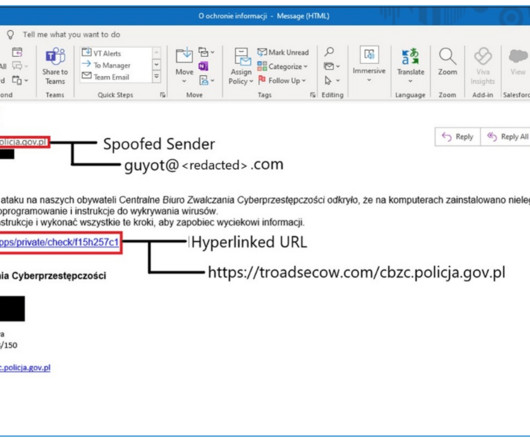
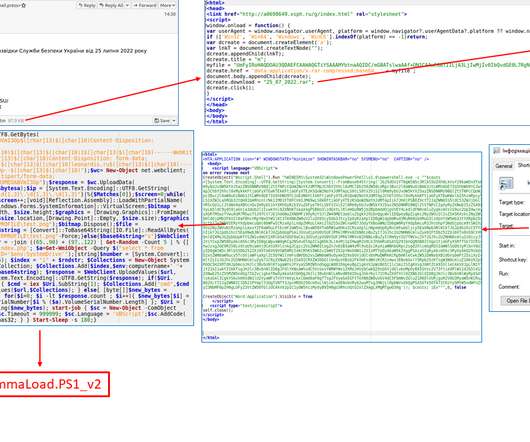
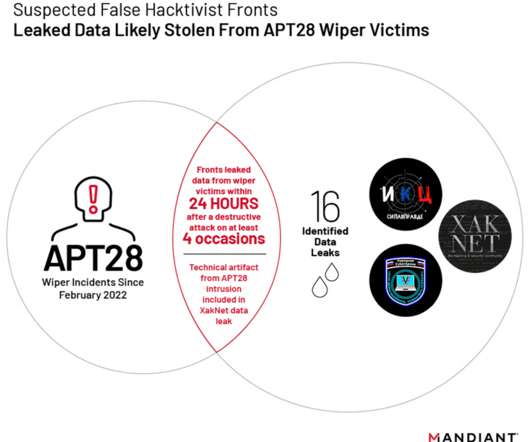
Hackers Used LLMs to Perform Tasks That Non-AI Tools Can Perform Nation-state hackers including Russian military intelligence and hackers backed by China have used OpenAI large language models for research and to craft phishing emails, the artificial intelligence company disclosed Tuesday in conjunction with major financial backer Microsoft.






































Let's personalize your content