Russian Military Intelligence Blamed for Blitzkrieg Hacks
Data Breach Today
DECEMBER 29, 2023
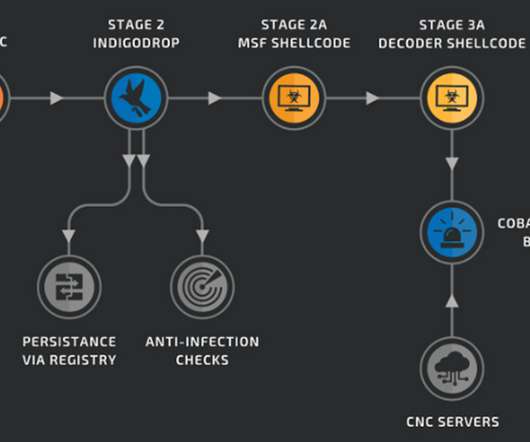
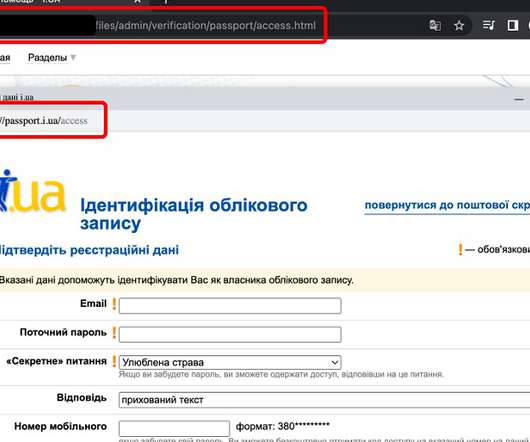
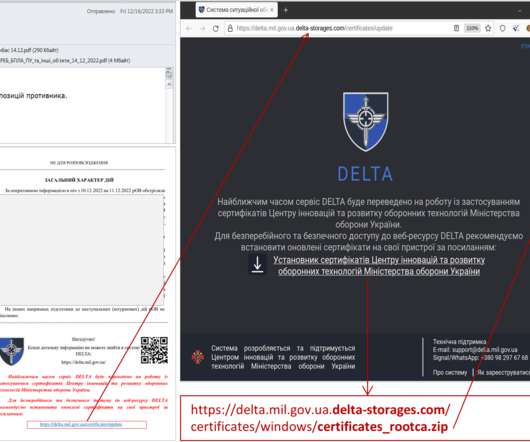
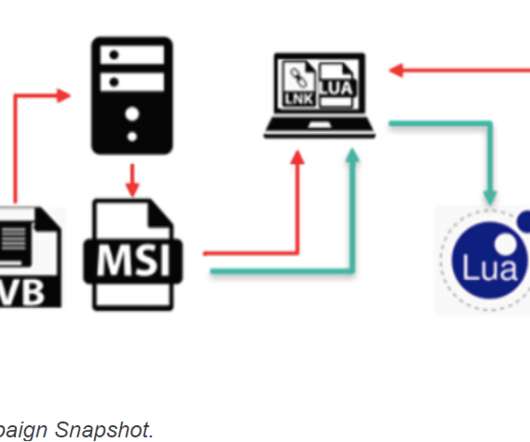
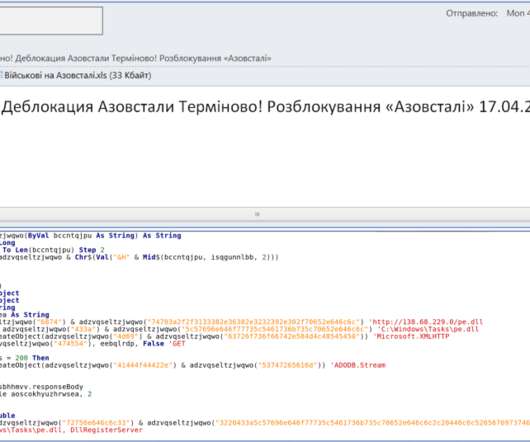
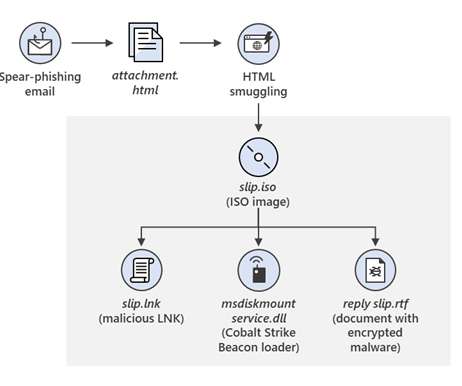
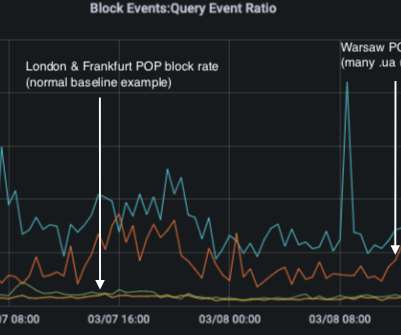
Ukrainian Cyber Defenders Trace Government Agency Hits to Phishing Campaign Ukrainian cyber defenders report that fast-acting Russian military intelligence hackers have been targeting government agencies as well as organizations in Poland using backdoor malware tied to phishing lures based on a fake letter from the Ukrainian deputy prime minister.










































Let's personalize your content