Operation In(ter)reception targets Military and Aerospace employees in Europe and the Middle East
Security Affairs
JUNE 17, 2020
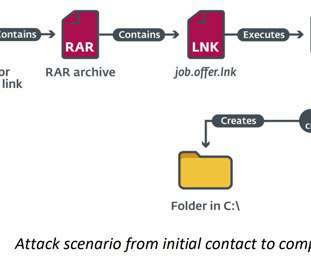
Experts uncovered a new cyber-espionage campaign, dubbed “ Operation In(ter)receptio n,” aimed at aerospace and military organizations in Europe and the Middle East. ” The attackers used password-protected RAR archive files as decoys purported to include a PDF document with details on the salary for specific job positions.















Let's personalize your content