The Week in Cyber Security and Data Privacy: 12 – 18 February 2024
IT Governance
FEBRUARY 21, 2024
Fowler sent a responsible disclosure notice when he discovered the database and it was secured the following day. Source New Manufacturing USA Yes 20,415 TECA Srl Source New Transport Italy Yes 16.7 Known records breached Zenlayer Source New Telecoms USA Yes 384,658,212 ASA Electronics Source New Engineering USA Yes 2.7





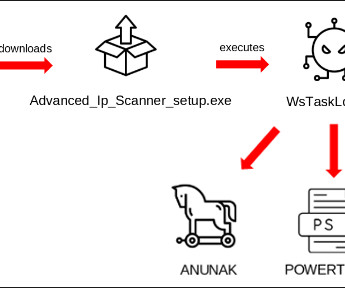

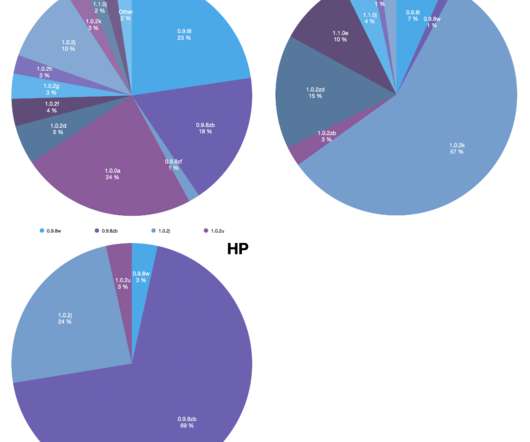
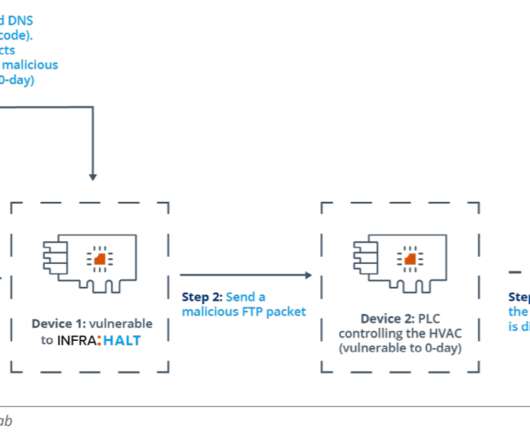








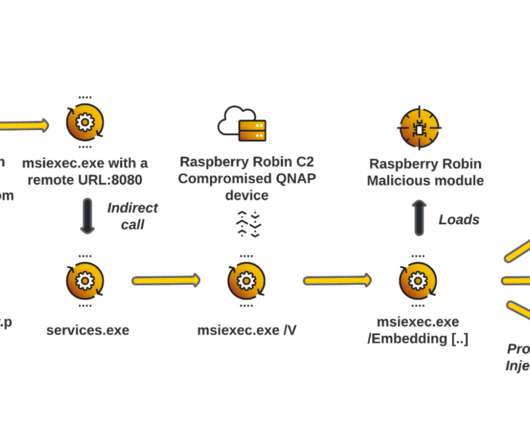

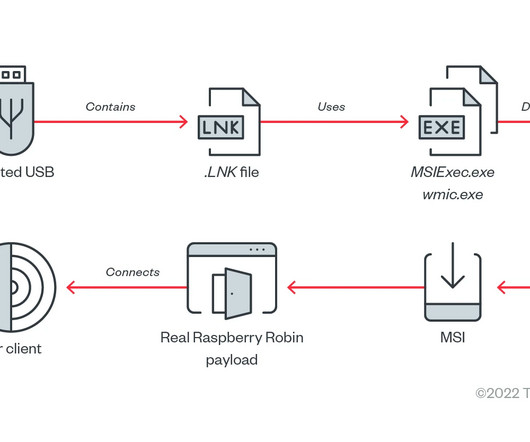
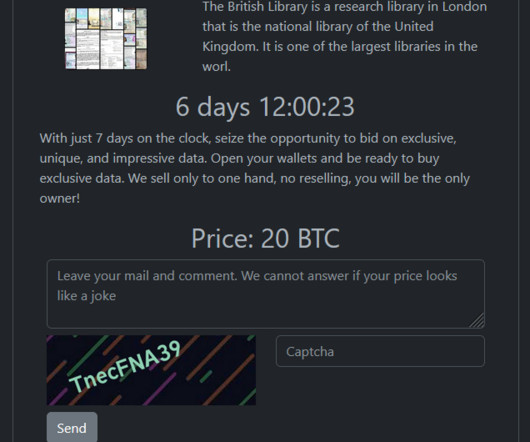
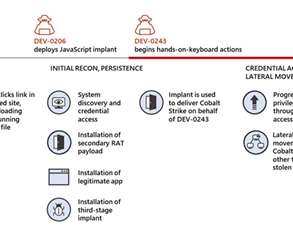


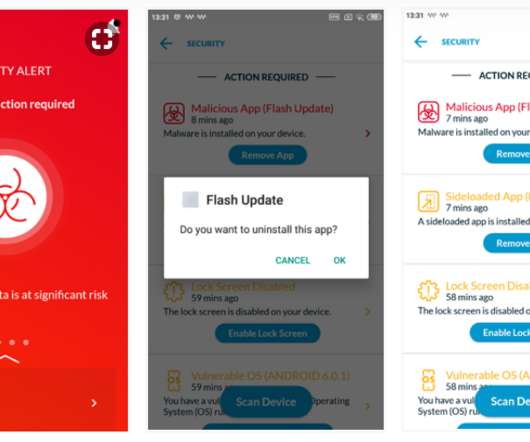



















Let's personalize your content