GUEST ESSAY: How to mitigate the latest, greatest phishing variant — spoofed QR codes
The Last Watchdog
NOVEMBER 6, 2023
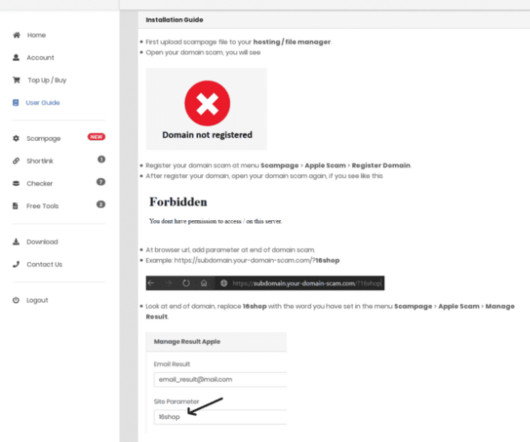
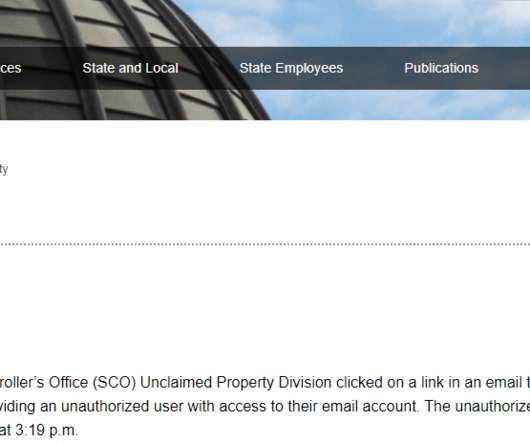
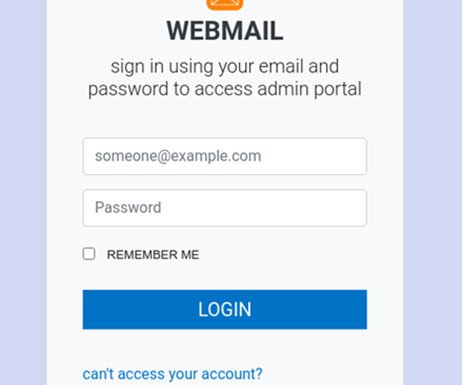
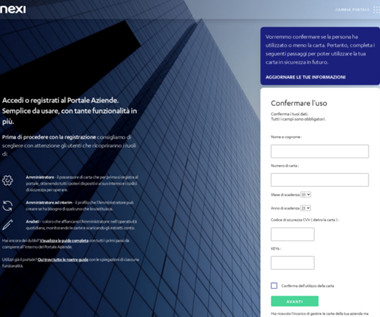
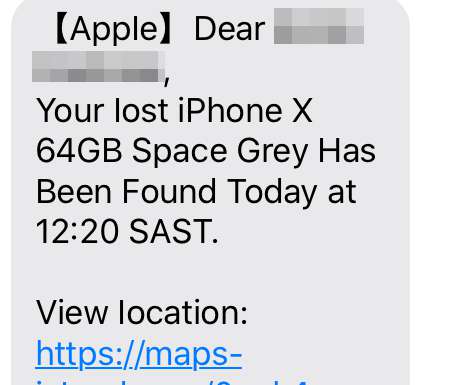
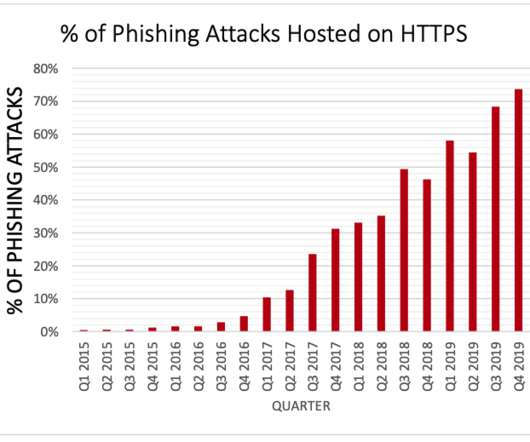
QR code phishing attacks started landing in inboxes around the world about six months ago. Scans slip through These attacks are so successful because many traditional email security tools focus only on text-scanning, allowing image-based attacks to slip through. This is a true reflection of the attack landscape.











































Let's personalize your content