GUEST ESSAY: How to mitigate the latest, greatest phishing variant — spoofed QR codes
The Last Watchdog
NOVEMBER 6, 2023
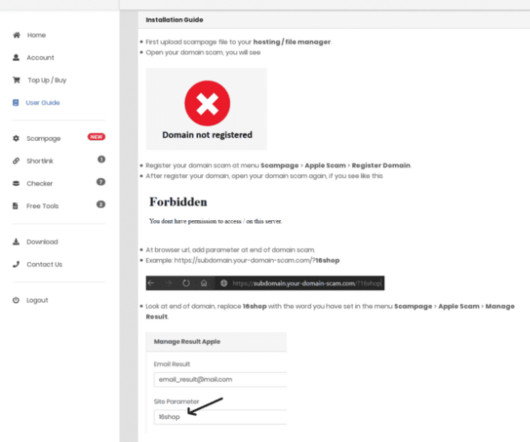
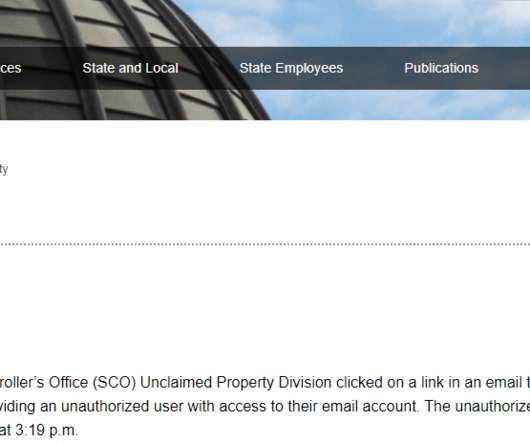
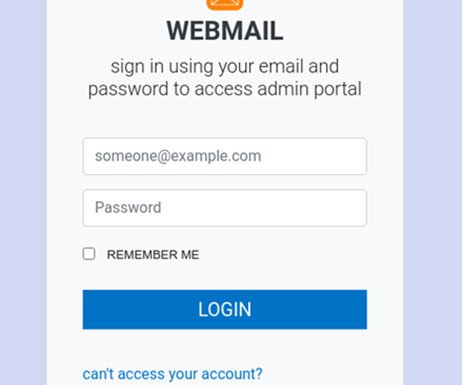
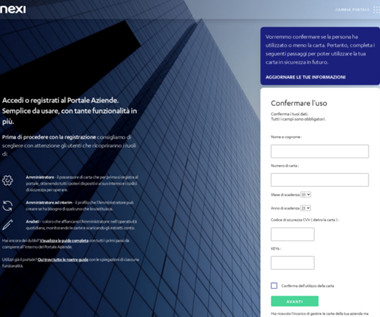
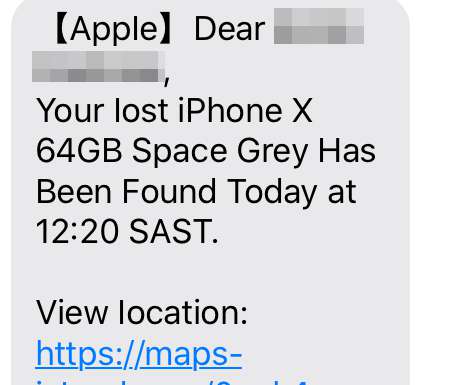
QR code phishing attacks started landing in inboxes around the world about six months ago. Best practices So how do you defend your enterprise against QR code phishing attacks? In June, we started seeing these types of attacks amongst our customer base. About the essayist: Allen Lieberman is the Chief Product Officer at Tessian.









































Let's personalize your content