Experian Glitch Exposing Credit Files Lasted 47 Days
Krebs on Security
JANUARY 25, 2023
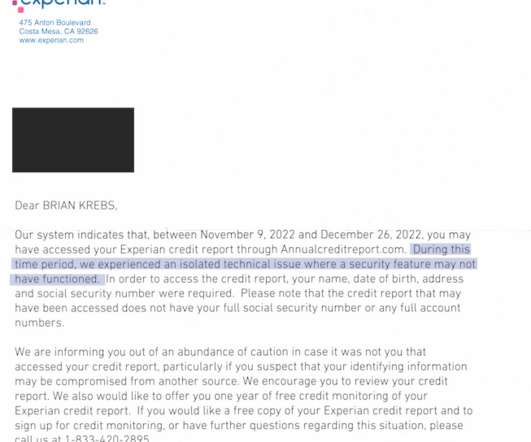
23, 2022, KrebsOnSecurity alerted big-three consumer credit reporting bureau Experian that identity thieves had worked out how to bypass its security and access any consumer’s full credit report — armed with nothing more than a person’s name, address, date of birth, and Social Security number. 9, 2022 and Dec.






















Let's personalize your content