New InfectedSlurs Mirai-based botnet exploits two zero-days
Security Affairs
NOVEMBER 22, 2023
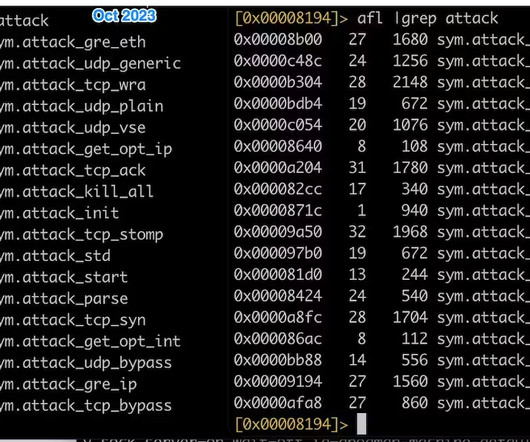
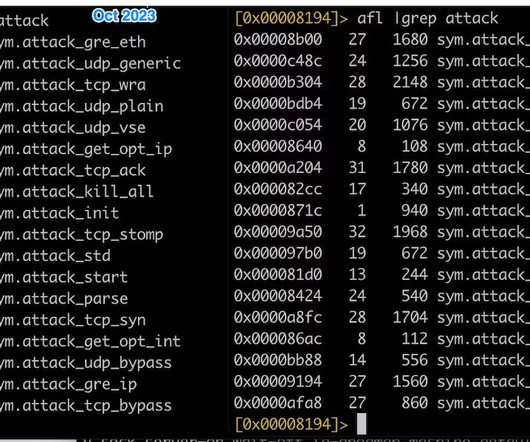
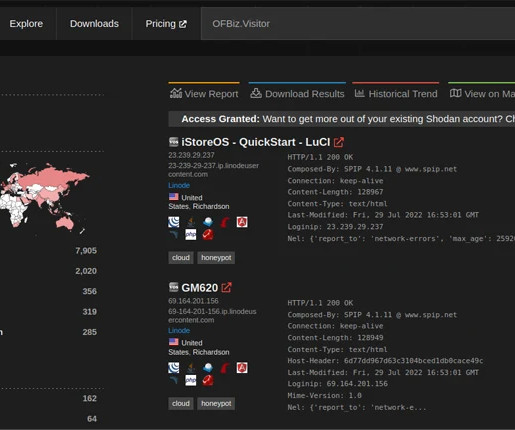
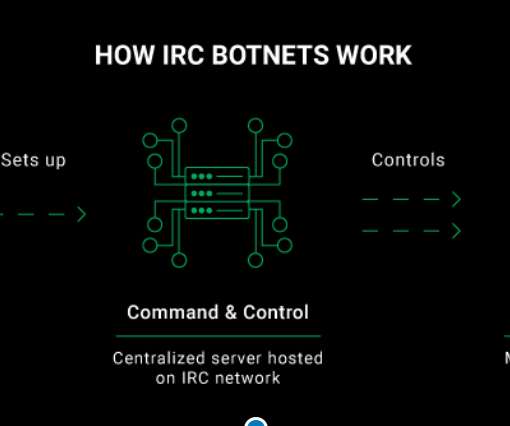
Mirai-based botnet InfectedSlurs has been spotted exploiting two zero-day RCE flaws to compromise routers and video recorder (NVR) devices. Akamai discovered a new Mirai-based DDoS botnet, named InfectedSlurs, actively exploiting two zero-day vulnerabilities to infect routers and video recorder (NVR) devices.

















Let's personalize your content