We infiltrated an IRC botnet. Here’s what we found
Security Affairs
NOVEMBER 19, 2020
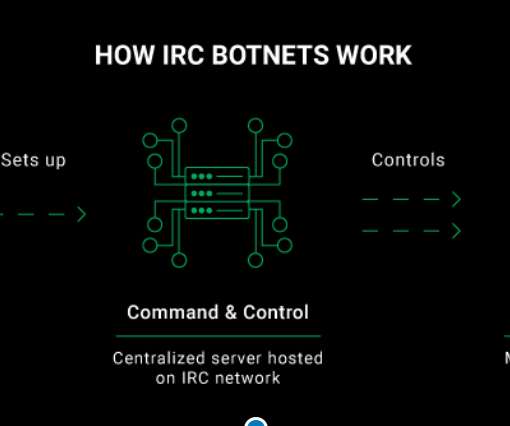
To conduct this investigation, a CyberNews researcher infiltrated an IRC botnet that we captured in one of our honeypots. Our honeypot setup. In cybersecurity terms, a honeypot is a decoy service or system that poses as a target for malicious actors. Here’s how it all happened. About this investigation.










Let's personalize your content