Indian Pharmaceutical Company Investigates Security Incident
Data Breach Today
OCTOBER 22, 2020
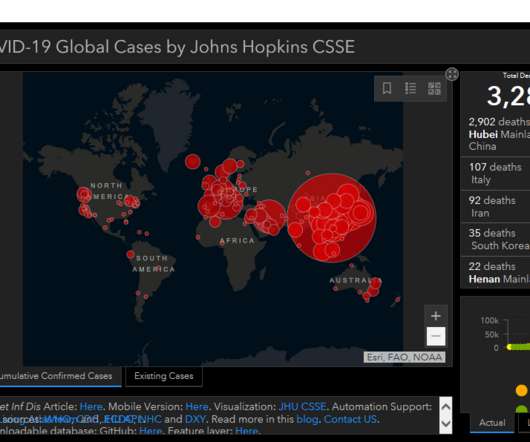
Reddy's Laboratories Says Plants in Four Countries Affected Dr. Reddy's Laboratories, a multinational pharmaceutical company based in India that's testing a COVID-19 vaccine, says it isolated its data center services Thursday following what it calls a "detected cyberattack."






































Let's personalize your content