National Safety Council data leak: Credentials of NASA, Tesla, DoJ, Verizon, and 2K others leaked by workplace safety organization
Security Affairs
AUGUST 31, 2023
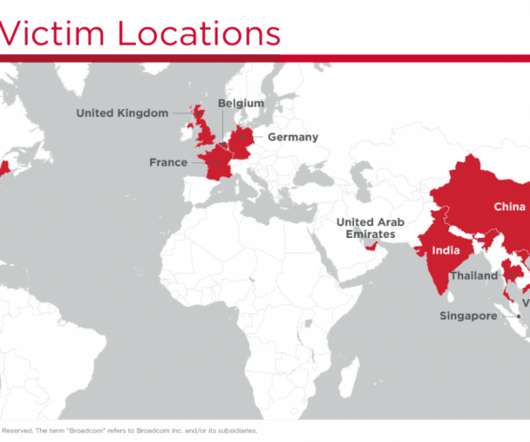
Leaked credentials could have been used for credential stuffing attacks, which try to log into companies’ internet-connected tools such as VPN portals, HR management platforms, or corporate emails. The vulnerability posed a risk not only to NSC systems but also to the companies using NSC services.




























Let's personalize your content