GUEST ESSAY: The drivers behind persistent ransomware — and defense tactics to deploy
The Last Watchdog
SEPTEMBER 7, 2022
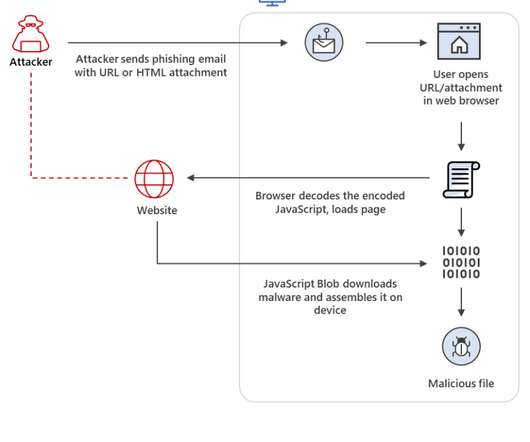
Healthcare and public health, financial services, and IT organizations are frequent targets, although businesses of all sizes can fall victim to these schemes. Likewise, lookalike and spoofed web domains and well-crafted phishing emails now easily trick employees into thinking they’re dealing with trustworthy sources.
















Let's personalize your content