New HiatusRAT campaign targets Taiwan and U.S. military procurement system
Security Affairs
AUGUST 21, 2023
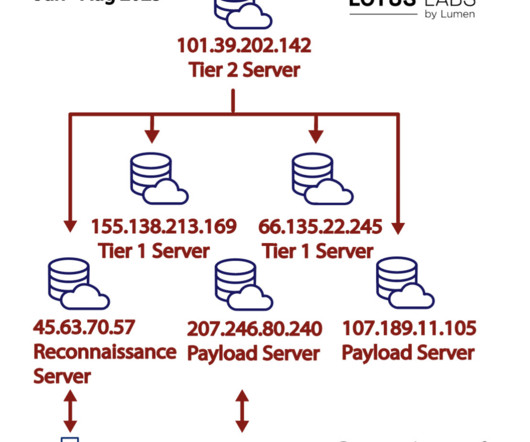
military procurement system. In June the group started a reconnaissance and targeting activity aimed at a U.S. military server used for contract proposals and submissions. “We recommend defense contractors exercise caution and monitor their networking devices for the presence of HiatusRAT. 57 155.138.213[.]169














Let's personalize your content