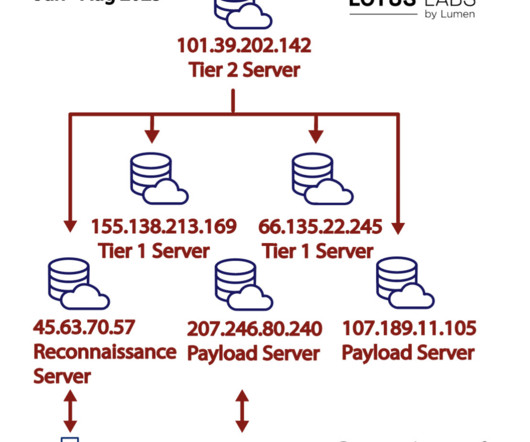
New HiatusRAT campaign targets Taiwan and U.S. military procurement system
Security Affairs
AUGUST 21, 2023
military procurement system. military procurement system and was spotted targeting Taiwan-based organizations The choice of the new targets in the latest campaign suggests a strategic interest of the People’s Republic of China according to the 2023 ODNI threat assessment. military server used for contract proposals and submissions.


















Let's personalize your content