From iPhone to NT AUTHORITYSYSTEM – exploit ‘Printconfig’ dll with a real-world example
Security Affairs
DECEMBER 15, 2019
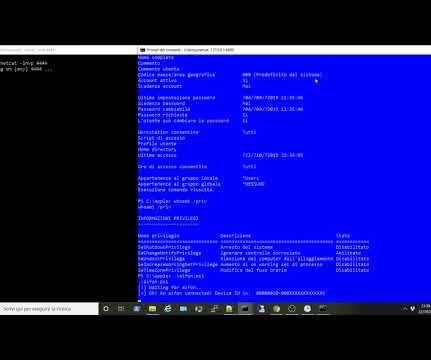
From iPhone to NT AUTHORITYSYSTEM – As promised in my previous post , I will show you how to exploit the “Printconfig” dll with a real world example. Standard Windows users do not need special privileges to create this type of links and we can use Forshaw’s utilties to manage them. Well, keep on reading… ( sorry no ).


















Let's personalize your content