New SPIKEDWINE APT group is targeting officials in Europe
Security Affairs
FEBRUARY 29, 2024
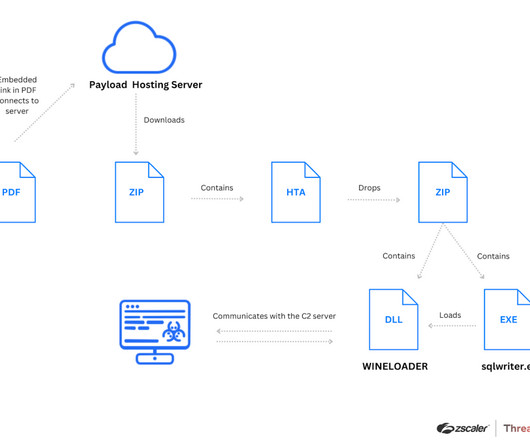
The cyberspies used a bait PDF document masqueraded as an invitation letter from the Ambassador of India, inviting diplomats to a wine-tasting event in February 2024. The ZIP archive contains an HTA file named wine.hta that contains obfuscated JavaScript code.




















Let's personalize your content