Cyber Security Awareness Month – Answering Google’s Most Commonly Asked Questions
Thales Cloud Protection & Licensing
OCTOBER 17, 2023
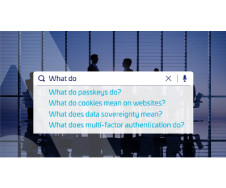
Cyber Security Awareness Month – Answering Google’s Most Commonly Asked Questions madhav Wed, 10/18/2023 - 05:25 This month is Cyber Security Awareness Month , highlighting how far security education needs to go in order to enable a secure interconnected world. Data Sovereignty What is data sovereignty?














Let's personalize your content