DeathRansom ransomware evolves encrypting files, but experts identified its author
Security Affairs
JANUARY 5, 2020
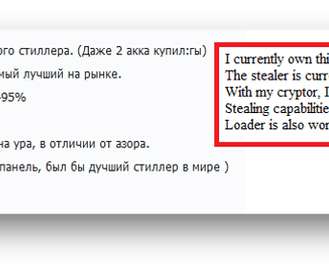
DeathRansom was considered fake ransomware due to the fact that it did not implement an effective encryption process, but now things are changing. DeathRansom is a ransomware family that was initially classified as a joke because it did not implement an effective encryption scheme. They share the naming pattern and infrastructure used.

























Let's personalize your content