A flaw in the encryption algorithm of Hive Ransomware allows retrieving encrypted files
Security Affairs
FEBRUARY 21, 2022
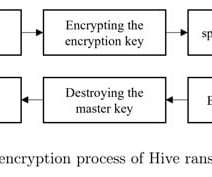
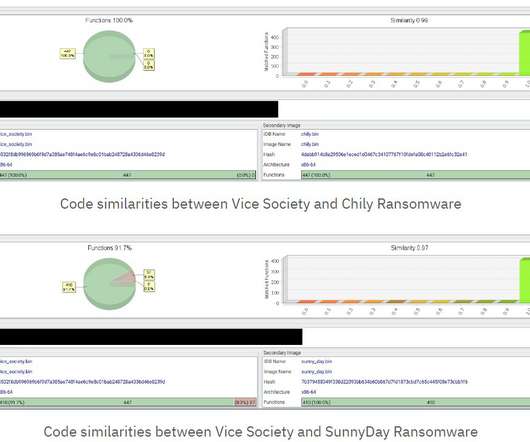
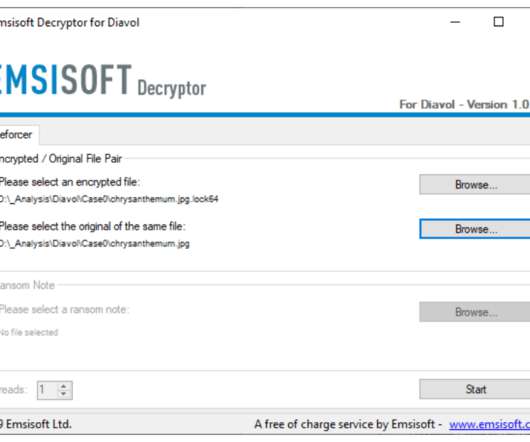
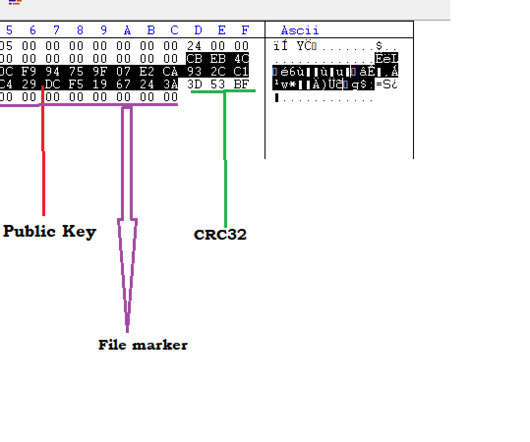
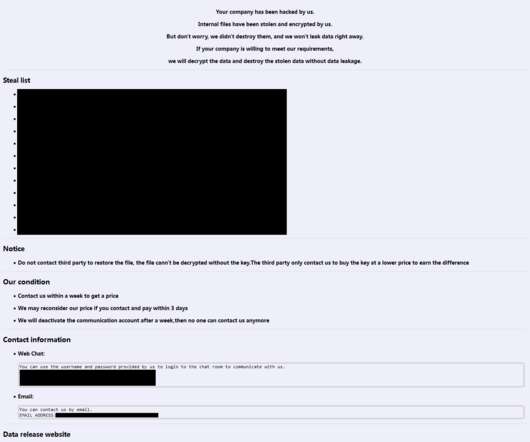
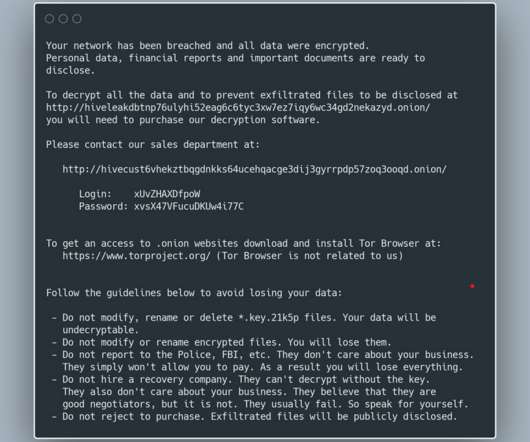
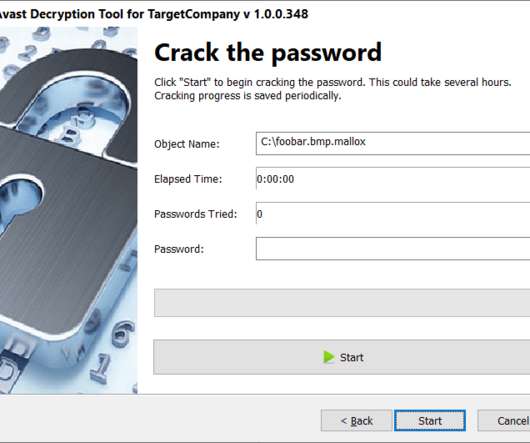
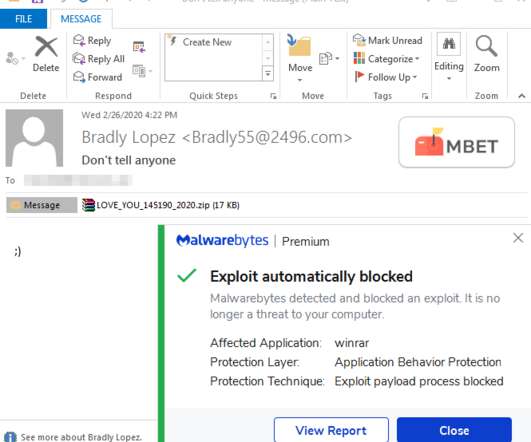
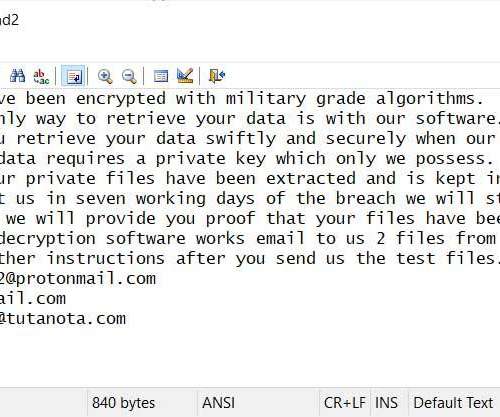
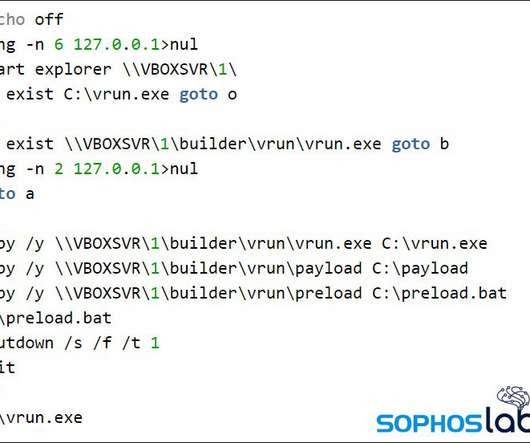
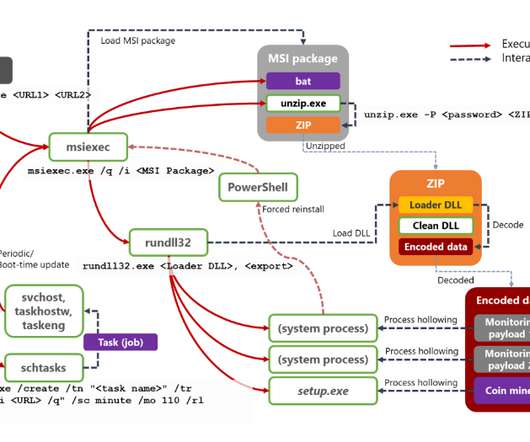
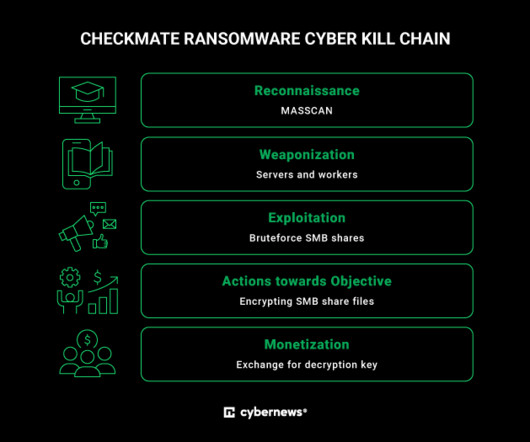
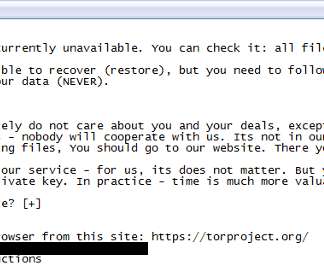
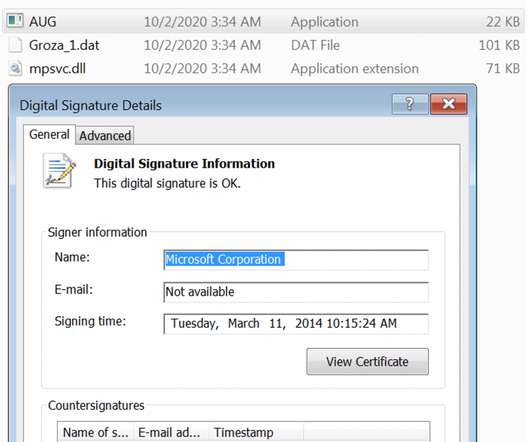
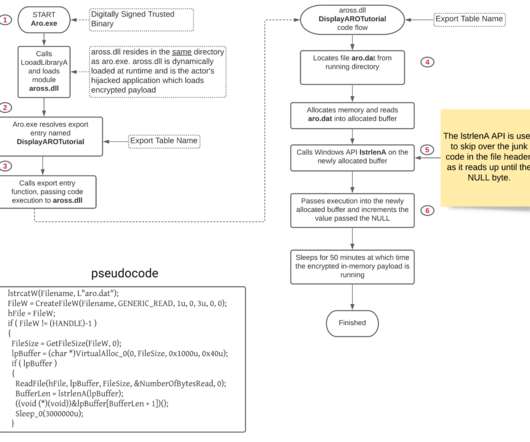
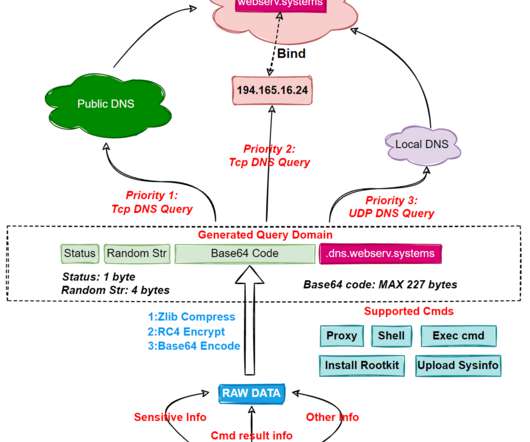
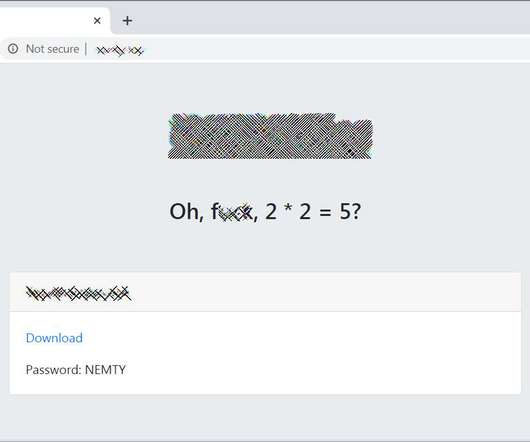
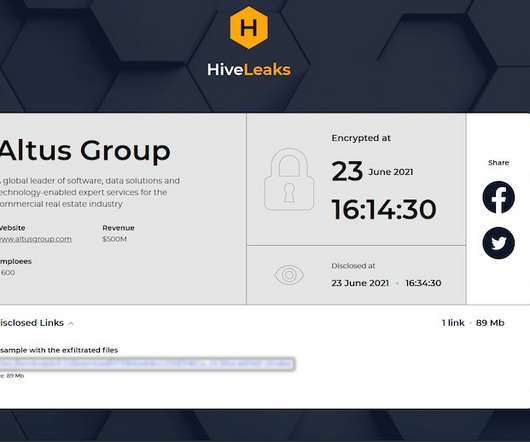
Researchers discovered a flaw in the encryption algorithm used by Hive ransomware that allowed them to decrypt data. Researchers discovered a flaw in the encryption algorithm used by Hive ransomware that allowed them to decrypt data without knowing the private key used by the gang to encrypt files. Pierluigi Paganini.






















Let's personalize your content