ENISA 2023 Threat Landscape Report: Key Findings and Recommendations
Thales Cloud Protection & Licensing
DECEMBER 4, 2023
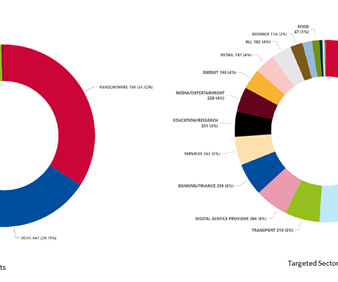
The report also highlights that ransomware attacks are becoming more targeted, with attackers focusing on high-value targets with particular emphasis on the Industrial and Manufacturing sectors. Ensure you maintain offline, encrypted data backups that are regularly tested, following your backup procedures.


























Let's personalize your content