The Clock To Q-Day Is Ticking: InfoSec Global and Thales Provide Collaborative Path to Quantum Readiness
Thales Cloud Protection & Licensing
FEBRUARY 19, 2024
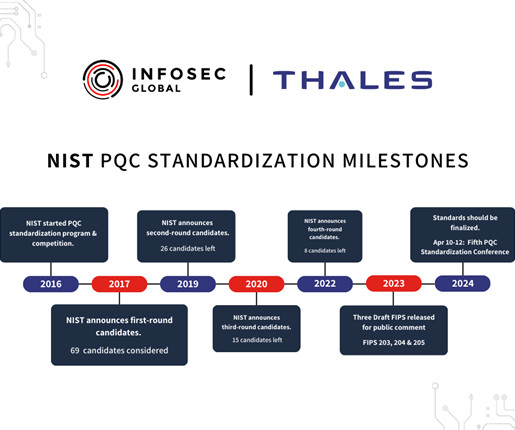
To counter HNDL, migrating critical systems to Post-Quantum Cryptography (PQC) provides encryption and authentication methods resistant to an attack from a cryptographically relevant quantum computer (CRQC). This vulnerability could expose sensitive enterprise information to risk. In the U.S.,


























Let's personalize your content