How China Hacked US Phone Networks
WIRED Threat Level
JUNE 11, 2022
Plus: Russia rattles its cyber sword, a huge Facebook phishing operation is uncovered, feds take down the SSNDOB marketplace, and more.

WIRED Threat Level
JUNE 11, 2022
Plus: Russia rattles its cyber sword, a huge Facebook phishing operation is uncovered, feds take down the SSNDOB marketplace, and more.

The Last Watchdog
JUNE 13, 2022
At the start of this year, analysts identified a number of trends driving the growth of cybersecurity. Among them: an expanding digital footprint, growing attack surfaces, and increasing government regulation. Related: Taking API proliferation seriously. Last year saw an unprecedented $21.8 billion in venture capital poured into cybersecurity companies globally.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Security Affairs
JUNE 13, 2022
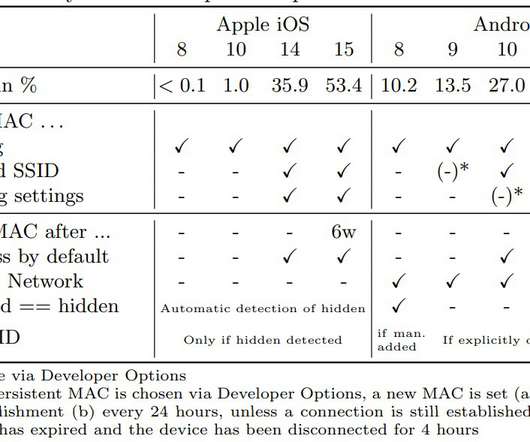
Researchers at the University of Hamburg demonstrated that WiFi connection probe requests expose users to track. A group of academics at the University of Hamburg (Germany) demonstrated that it is possible to use WiFi connection probe requests to identify and track devices and thereby their users. Mobile devices transmit probe requests to receive information about nearby Wi-Fi networks and establish a Wi-Fi connection.

Data Breach Today
JUNE 17, 2022
DXC Technology's Michael Baker on Top Threats, Recruitment Tips, Career Advice Threat watch: The ongoing Russia-Ukraine war continues to pose both direct and indirect risks to enterprise networks, says Michael Baker, vice president and IT CISO of IT services and consulting firm DXC Technology. He also discusses recruiting and retaining new talent.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.
Krebs on Security
JUNE 14, 2022
Cybercrime groups that specialize in stealing corporate data and demanding a ransom not to publish it have tried countless approaches to shaming their victims into paying. The latest innovation in ratcheting up the heat comes from the ALPHV/BlackCat ransomware group, which has traditionally published any stolen victim data on the Dark Web. Today, however, the group began publishing individual victim websites on the public Internet, with the leaked data made available in an easily searchable form
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
Security Affairs
JUNE 11, 2022
Iran-linked Lyceum APT group uses a new.NET-based DNS backdoor to target organizations in the energy and telecommunication sectors. The Iran-linked Lyceum APT group, aka Hexane or Spilrin, used a new.NET-based DNS backdoor in a campaign aimed at companies in the energy and telecommunication sectors, ZScaler researchers warn. The activity of the Lyceum APT group was first documented earlier in August 2019 by researchers at ICS security firm Dragos which tracked it as Hexane.

Data Breach Today
JUNE 16, 2022
The latest edition of the ISMG Security Report includes highlights and observations from RSA Conference 2022, including a key message from RSA CEO Rohit Ghai. It also discusses the value of automation and the Cybersecurity and Infrastructure Security Agency's mission to grow cyber talent.

Krebs on Security
JUNE 15, 2022
Microsoft on Tuesday released software updates to fix 60 security vulnerabilities in its Windows operating systems and other software, including a zero-day flaw in all supported Microsoft Office versions on all flavors of Windows that’s seen active exploitation for at least two months now. On a lighter note, Microsoft is officially retiring its Internet Explorer (IE) web browser, which turns 27 years old this year.

eSecurity Planet
JUNE 16, 2022
A cyberattack is any action taken by a cyber criminal in an attempt to illegally gain control of a computer, device, network, or system with malicious intent. Cyber criminals may damage, destroy, steal, encrypt, expose, or leak data as well as cause harm to a system. Cyberattacks are on the rise, with cyber criminal trends and techniques becoming increasingly sophisticated and creative.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.
Security Affairs
JUNE 12, 2022
Ransomware gangs are actively exploiting CVE-2022-26134 remote code execution (RCE) flaw in Atlassian Confluence Server and Data Center. Multiple ransomware groups are actively exploiting the recently disclosed remote code execution (RCE) vulnerability, tracked as CVE-2022-26134 , affecting Atlassian Confluence Server and Data Center. Proof-of-concept exploits for the CVE-2022-26134 vulnerability have been released online, Bleeping Computer reported that starting from Friday afternoon, a proo

Data Breach Today
JUNE 17, 2022
The State of Passwordless in 2022, New Identity Technologies In the latest weekly update, Jeremy Grant, coordinator of the Better Identity Coalition, joins three editors at ISMG to discuss important cybersecurity issues, including where we are with passwordless, if we are getting closer to a U.S. federal privacy law, and next-gen authentication technologies.

Krebs on Security
JUNE 14, 2022
A 33-year-old Illinois man was sentenced to two years in prison today following his conviction last year for operating services that allowed paying customers to launch powerful distributed denial-of-service (DDoS) attacks against hundreds of thousands of Internet users and websites. The user interface for Downthem[.]org. Matthew Gatrel of St. Charles, Ill. was found guilty for violations of the Computer Fraud and Abuse Act (CFAA) related to his operation of downthem[.]org and ampnode[.]com , two

KnowBe4
JUNE 13, 2022
Researchers at PIXM have uncovered a major Facebook Messenger phishing scam that’s “potentially impacted hundreds of millions of Facebook users.” More than eight million people have visited just one of these phishing pages so far this year.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.
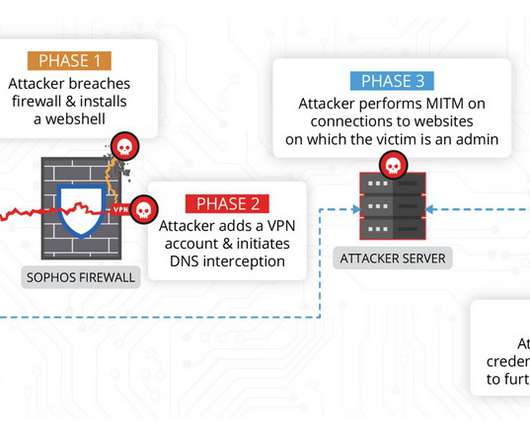
Security Affairs
JUNE 17, 2022
China-linked threat actors exploited the zero-day flaw CVE-2022-1040 in Sophos Firewall weeks before it was fixed by the security vendor. Volexity researchers discovered that the zero-day vulnerability, tracked as CVE-2022-1040 , in Sophos Firewall was exploited by Chinese threat actors to compromise a company and cloud-hosted web servers it was operating.

Data Breach Today
JUNE 15, 2022
CISO of Maricopa County, Arizona on Strengthening Election Security "Social media is probably the newest and most impactful thing that we've seen from a cybersecurity perspective at Maricopa County," says its CISO, Lester Godsey. The only response to misinformation and disinformation campaigns, he says, is to use the same platform and respond with the facts.

Schneier on Security
JUNE 16, 2022
Interesting research: “ Sponge Examples: Energy-Latency Attacks on Neural Networks “: Abstract: The high energy costs of neural network training and inference led to the use of acceleration hardware such as GPUs and TPUs. While such devices enable us to train large-scale neural networks in datacenters and deploy them on edge devices, their designers’ focus so far is on average-case performance.

KnowBe4
JUNE 14, 2022
Attackers are taking advantage of the current news about monkeypox to trick people into clicking on malicious links, Pickr reports. Researchers at Mimecast have spotted a phishing campaign that impersonates companies in an attempt to trick employees into visiting phony health safety sites that steal their information.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Data Matters
JUNE 14, 2022
Certification by a professional institution is one of the mechanisms permitted under China’s Personal Information Protection Law ( PIPL ) to legitimizing cross-border transfers of personal information. Other permitted mechanisms include governmental security review and standard contractual clauses to be issued by Chinese government. However, to date, there have been no clear rules on the criteria and procedures for obtaining the PIPL certification.

Data Breach Today
JUNE 17, 2022
KnowBe4's Roger Grimes on Why MFA Alone Isn't a Successful Hack Prevention Strategy Phishing is no longer restricted to just emails. As attackers broaden their arsenal, businesses today also need to be on the lookout for impersonation attempts via SMS text messages or voice calls, says Roger Grimes, a data-driven defense evangelist at KnowBe4.

Schneier on Security
JUNE 17, 2022
We’ve always known that phones—and the people carrying them—can be uniquely identified from their Bluetooth signatures, and that we need security techniques to prevent that. This new research shows that that’s not enough. Computer scientists at the University of California San Diego proved in a study published May 24 that minute imperfections in phones caused during manufacturing create a unique Bluetooth beacon , one that establishes a digital signature or fingerprint di

Security Affairs
JUNE 12, 2022
A new round of the weekly Security Affairs newsletter arrived! Every week the best security articles from Security Affairs for free in your email box. If you want to also receive for free the newsletter with the international press subscribe here. Ransomware gangs are exploiting CVE-2022-26134 RCE in Atlassian Confluence servers HID Mercury Access Controller flaws could allow to unlock Doors Iran-linked Lyceum APT adds a new.NET DNS Backdoor to its arsenal PACMAN, a new attack technique against

Advertisement
Are you trying to decide which entity resolution capabilities you need? It can be confusing to determine which features are most important for your project. And sometimes key features are overlooked. Get the Entity Resolution Evaluation Checklist to make sure you’ve thought of everything to make your project a success! The list was created by Senzing’s team of leading entity resolution experts, based on their real-world experience.

Collibra
JUNE 15, 2022
We are incredibly honored and excited to share that Great Place to Work and Fortune magazine have included Collibra as one of this year’s Best Workplaces in New York! This is our first time being named to this list, coming in at #4, and we are incredibly grateful to our employees for their contributions to our culture and work environment – leading to this recognition. .

Data Breach Today
JUNE 15, 2022
Incident Is Latest on Growing List of Recent Major Healthcare Data Hacks An Arizona medical center that suffered a ransomware attack in April has begun notifying 700,000 individuals of a data breach compromising sensitive medical and personal information. The incident is among the latest major health data breaches involving ransomware.

IT Governance
JUNE 16, 2022
Channel 4 has faced heavy criticism after broadcasting a fake emergency news message warning that the UK is about to be hit by a catastrophic cyber attack. The message was filmed at what appeared to be GCHQ – the UK government’s intelligence and security headquarters – and informed viewers that Britain’s energy and water supplies could be cut off by an imminent attack.

eSecurity Planet
JUNE 14, 2022
With the plunge in tech stocks and the freeze in the IPO market, the funding environment for cybersecurity startups has come under pressure. According to Pitchbook, the amount of venture capital investment in the first quarter was off by 35.8% to $5.1 billion on a quarter-over-quarter basis. The median late-stage valuation fell by 26.1%. VCs are certainly getting pickier with their investments.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Data Matters
JUNE 13, 2022
Algorithms touch upon multiple aspects of digital life, and their use potentially falls within several separate – though converging – regulatory systems. More than ever, a ‘joined up’ approach is required to assess them, and the UK’s main regulators are working together to try to formulate a coherent policy, setting an interesting example that could be a template for global approaches to digital regulation.
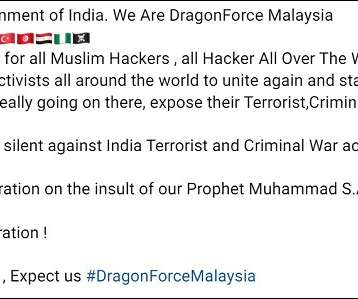
Data Breach Today
JUNE 13, 2022
DragonForce Malaysia's Alleged Victim List Comprises Government, Private Entities Hacktivist group DragonForce Malaysia says it hacked and defaced about 70 Indian government and private sector organizations' websites in a dayslong attack last week. The attacks were reportedly payback for anti-Muslim remarks made by a spokesperson of India's ruling political party.

Hunton Privacy
JUNE 14, 2022
On April 29, 2022, the National Information Security Standardization Technical Committee of China issued a draft version of the Cybersecurity Standard Practice Guidelines – Technical Specification on Certification of Personal Information Cross-border Transfer Activities (the “Guidelines”). The public comment period for the Guidelines closed May 13, 2022.
Let's personalize your content