Magecart gang hides PHP-based web shells in favicons
Security Affairs
MAY 14, 2021
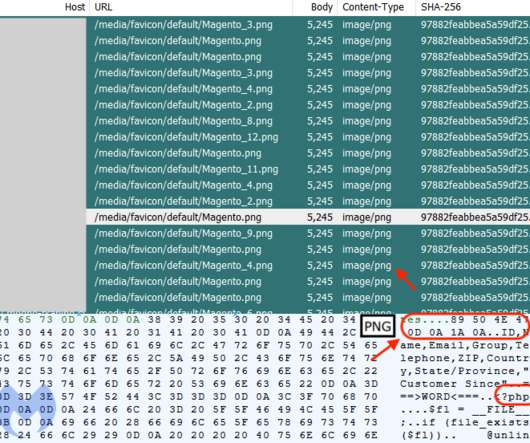
The web shells employed in the attacks are tracked as Smilodon or Megalodon , they dynamically load JavaScript skimming code via server-side requests into online stores. Threat actors edited the shortcut icon tags with a path to the fake PNG file. This technique allows bypassing most client-side security tools.

















Let's personalize your content