Why Criminals Keep Reusing Leaked Ransomware Builders
Data Breach Today
AUGUST 30, 2023
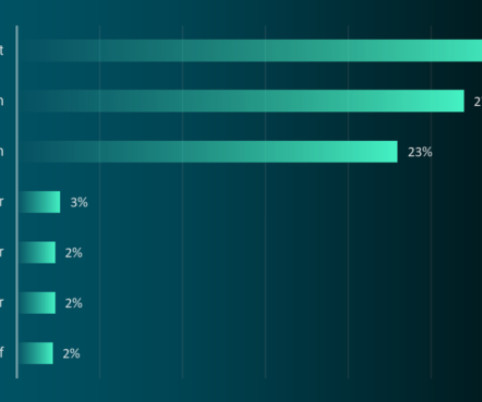
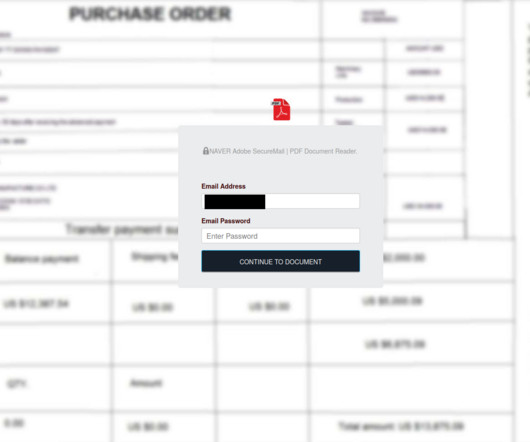
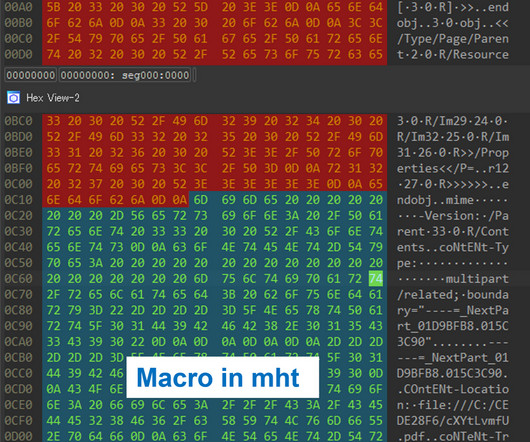
Blame Police Crackdowns on Big Names, Hacker Thrift, Ransomware Grifters in Trouble What's behind the a profusion of reported attacks involving stolen or reused strains of ransomware? Blame a variety of factors, including law enforcement crackdowns, evolving ransomware business models and at least one case of a ransomware group leader with poor morale building skills.




































Let's personalize your content