Teach Two Things to Decrease Phishing Attack Success
KnowBe4
AUGUST 24, 2022
We know everyone is busy. Everyone already has too much on their plate and is trying to learn as much as they can every day.

KnowBe4
AUGUST 24, 2022
We know everyone is busy. Everyone already has too much on their plate and is trying to learn as much as they can every day.

Data Breach Today
AUGUST 24, 2022
Takeaway: Behind-the-Scenes Security Reality at Well-Known Brands Not Always Pretty Cybersecurity experts have been reacting to industry veteran Peiter Zatko's allegations of poor information security practices at Twitter, with many noting that he's hardly the first expert to have been hired to remedy serious problems, only to say they were prevented from doing their job.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
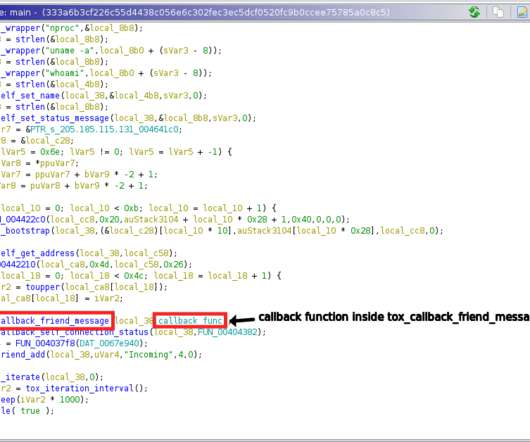
Security Affairs
AUGUST 24, 2022
Threat actors are using the Tox peer-to-peer instant messaging service as a command-and-control server, Uptycs researchers reported. Tox is a peer-to-peer serverless instant messaging services that uses NaCl for encryption and decryption. Uptycs researchers reported that threat actors have started using the Tox peer-to-peer instant messaging service as a command-and-control server.

Data Breach Today
AUGUST 24, 2022
Cyfirma Finds 80,000 Unpatched Chinese-made Cameras in Online Sweep An online search by cybersecurity firm Cyfirma found more than 80,000 unpatched cameras made by Hangzhou Hikvision Digital Technology Co. Attackers could exploit the vulnerability to add the cameras to a botnet or as a launching point for lateral movement deeper into the camera operator's network.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

Security Affairs
AUGUST 24, 2022
The streaming media platform Plex is urging its users to reset passwords after threat actors gained access to its database. Plex is an American streaming media service and a client–server media player platform. The company disclosed a data breach after threat actors have access to a limited subset of data stored in a compromised database. Exposed data includes emails, usernames, and encrypted passwords.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.

Dark Reading
AUGUST 24, 2022
The bug tracked as CVE-2022-0028 allows attackers to hijack firewalls without authentication, in order to mount DDoS hits on their targets of choice.

Data Breach Today
AUGUST 24, 2022
BioCatch's JP Blaho on Key Trends Emerging in New Incidents, Investigations Among the hottest cybercrime trends globally: P2P fraud. JP Blaho of BioCatch discusses the latest scams, including Zelle fraud, and differences in incidents, investigations and regulatory requirements in the U.S. and other global hotspots.

Schneier on Security
AUGUST 24, 2022
Peiter Zatko, aka Mudge, has filed a whistleblower complaint with the SEC against Twitter, claiming that they violated an eleven-year-old FTC settlement by having lousy security. And he should know; he was Twitter’s chief security officer until he was fired in January. The Washington Post has the scoop (with documents) and companion backgrounder.

Data Breach Today
AUGUST 24, 2022
Tool Can Steal Gmail, Yahoo! and Microsoft Outlook Emails An Iranian government-backed hacking group known as Charming Kitten has updated its malware arsenal to include an email inbox scrapping tool, proof of the group's dedication to developing and maintaining purpose-built capabilities. The tool spoofs the user agent to look like an outdated browser.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

Security Affairs
AUGUST 24, 2022
VMware this week released patches to address an important-severity vulnerability in the VMware Tools suite of utilities. The virtualization giant VMware this week released patches to address an important-severity flaw, tracked as CVE-2022-31676, which impacts the VMware Tools suite of utilities. VMware Tools is a set of services and modules that enable several features in company products for better management of, and seamless user interactions with, guests operating systems.

Data Breach Today
AUGUST 24, 2022
Settlement Shows Challenges of Properly Disposing of Patient Info A breach investigation into an incident initially appearing to affect only one individual has turned into a $300,640 HIPAA settlement for a dermatology practice that was subsequently discovered to be improperly disposing many patient information for more than a decade.
Security Affairs
AUGUST 24, 2022
The threat actors behind a large-scale adversary-in-the-middle (AiTM) phishing campaign now target Google G Suite users. The threat actors behind a large-scale adversary-in-the-middle (AiTM) phishing campaign targeting enterprise users of Microsoft email services were spotted targeting Google G Suite users. In AiTM phishing, threat actors set up a proxy server between a target user and the website the user wishes to visit, which is the phishing site under the control of the attackers.

Dark Reading
AUGUST 24, 2022
In a widespread campaign, threat actors use a compromised Dynamics 365 Customer Voice business account and a link posing as a survey to steal Microsoft 365 credentials.

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Security Affairs
AUGUST 24, 2022
A French hospital, the Center Hospitalier Sud Francilien (CHSF), suffered a cyberattack on Sunday and was forced to refer patients to other structures. The Center Hospitalier Sud Francilien (CHSF), a hospital southeast of Paris, has suffered a ransomware attack over the weekend. The attack disrupted the emergency services and surgeries and forced the hospital to refer patients to other structures.

Dark Reading
AUGUST 24, 2022
An insider threat or remote attacker with initial access could exploit CVE-2022-31676 to steal sensitive data and scoop up user credentials for follow-on attacks.

KnowBe4
AUGUST 24, 2022
There are, famously, three things you can do with risk: accept it, mitigate it, or transfer it. And you transfer risk by buying insurance against it.

IBM Big Data Hub
AUGUST 24, 2022
Forward thinking businesses see the value and potential that multicloud adoption offers. The only question is, how do you ensure effective ways of breaking down data silos and bringing data together for self-service access? It starts by modernizing your data integration capabilities – ensuring disparate data sources and cloud environments can come together to deliver data in real time and fuel AI initiatives.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Dark Reading
AUGUST 24, 2022
SolarWinds CISO Tim Brown explains how organizations can prepare for eventualities like the nation-state attack on his company’s software.

WIRED Threat Level
AUGUST 24, 2022
Without robust federal protections, the country's widespread mass surveillance systems could be used against citizens like never before.

Dark Reading
AUGUST 24, 2022
Center Hospitalier Sud Francilien (CHSF), a hospital outside of Paris, has redirected incoming patients to other medical facilities in the wake of a ransomware attack that began on Aug. 21.

Threatpost
AUGUST 24, 2022
Twitter is blasted for security and privacy lapses by the company’s former head of security who alleges the social media giant’s actions amount to a national security risk.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.

Dark Reading
AUGUST 24, 2022
Avoid the disconnect between seeing the value in threat modeling and actually doing it with coaching, collaboration, and integration. Key to making it "everybody's thing" is communication between security and development teams.

OpenText Information Management
AUGUST 24, 2022
These days, you can’t throw a rock without hitting someone who is talking about the Metaverse. The c-suite might be discussing the merits of blockchain for personalization and security. Developers might be elaborating on the necessity of decentralization of Web3 elements to create a free and open experience (not one lorded over by big tech … The post Supply chain in the age of the metaverse appeared first on OpenText Blogs.

Dark Reading
AUGUST 24, 2022
The Russia-backed Nobelium APT has pioneered a post-exploitation tool allowing attackers to authenticate as any user.

Hunton Privacy
AUGUST 24, 2022
On August 23, 2022, the Federal Trade Commission announced it is seeking additional public comment on “how children are affected by digital advertising and marketing messages that may blur the line between ads and entertainment” in conjunction with its “Protecting Kids from Stealth Advertising in Digital Media” event on October 19, 2022. The event will focus on manipulative marketing practices targeted towards children, particularly those related to influencer marketing and online games.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Dark Reading
AUGUST 24, 2022
Increasing complexity in IT continues to lead to breaches and compromises, highlighting the need for more holistic approaches to cyber protection.

OpenText Information Management
AUGUST 24, 2022
The SocGholish campaign is suspected to be linked to the Russian threat actor known as “Evil Corp”. The threat actors are known to drop HTML code into outdated or vulnerable websites. When a user visits the compromised website, the code generates a pop-up within the browser attempting to trick the user into believing their browser … The post NetSupport Remote Access Trojan (RAT) delivered through fake browser updates by SocGholish threat actors appeared first on OpenText Blogs.

Dark Reading
AUGUST 24, 2022
Every organization is on a zero-trust journey. Learn about how critical identity is to your security evolution, and how your organization can move forward.
Let's personalize your content