Ubiquiti: Change Your Password, Enable 2FA
Krebs on Security
JANUARY 11, 2021
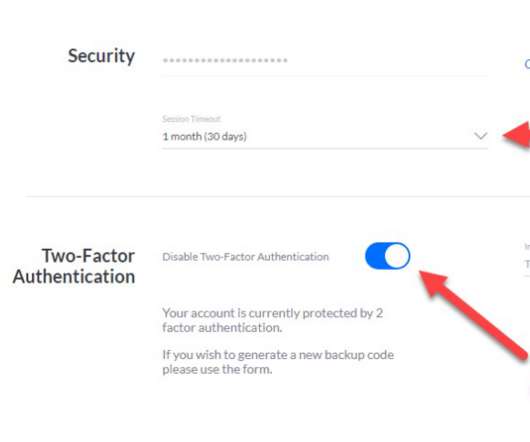
Ubiquiti , a major vendor of cloud-enabled Internet of Things (IoT) devices such as routers, network video recorders, security cameras and access control systems, is urging customers to change their passwords and enable multi-factor authentication. The company says an incident at a third-party cloud provider may have exposed customer account information and credentials used to remotely manage Ubiquiti gear.






































Let's personalize your content