LockBit Group Goes From Denial to Bargaining Over Royal Mail
Data Breach Today
FEBRUARY 7, 2023
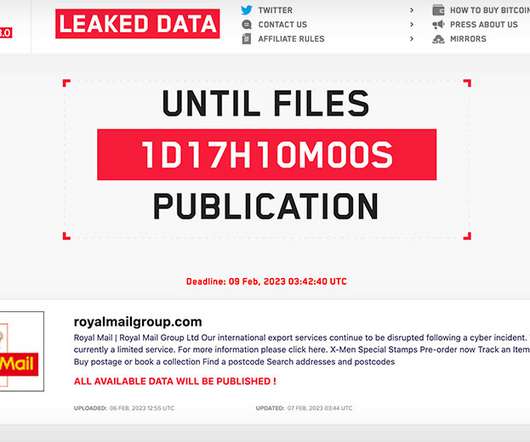
Ransomware Remains a Royal Pain, as Criminals' Latest Extortion Attempt Highlights The LockBit group has gone from denying it had any involvement in the ransomware attack on Britain's Royal Mail, to trying to bargain for a ransom. The ransomware group's site now lists Royal Mail as a victim, and demands it pay a ransom or see stolen data get dumped.







































Let's personalize your content