Microsoft Patches Zero-Day Bug Exploited by Ransomware Group
Data Breach Today
APRIL 12, 2023
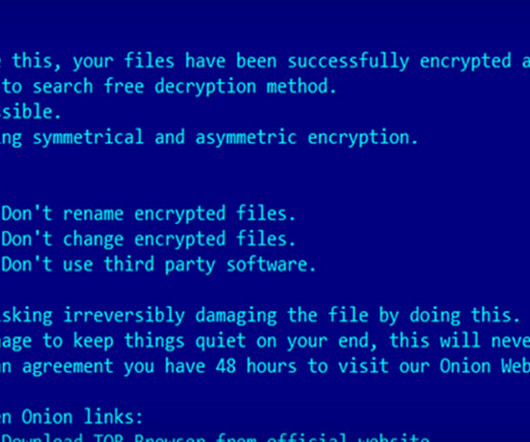
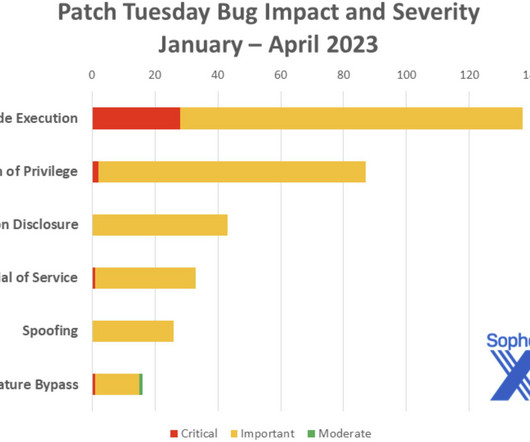
Attackers Drop Nokoyawa Ransomware; Experts See Increasing Criminal Sophistication Microsoft has issued fixes for 114 vulnerabilities, including patching a zero-day flaw being actively exploited by a ransomware group and updating guidance to block a vulnerability from 2013 that was recently exploited for the software supply chain attack on 3CX users, attributed to North Korea.






































Let's personalize your content