ITRC: Lack of Details in Data Breach Notices on the Rise
Data Breach Today
APRIL 24, 2023
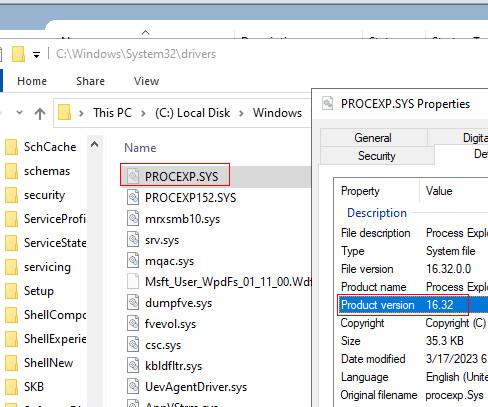
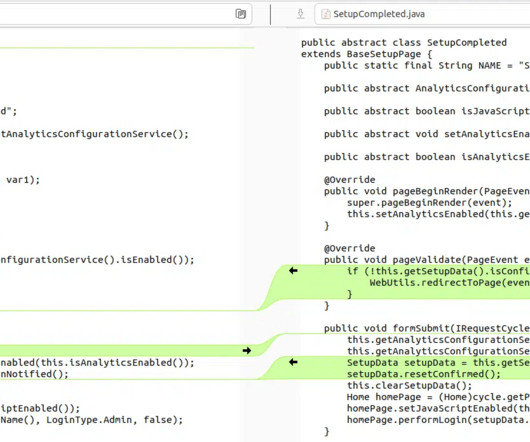
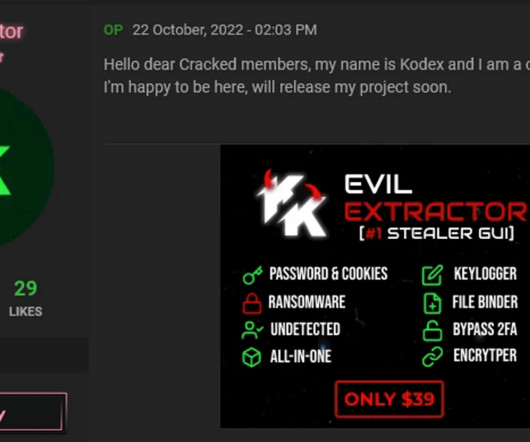
James E. Lee Shares 2023 Q1 Data Breach Report Highlights According to findings from the Identity Theft Resource Center's 2023 Q1 Data Breach Report, the number of publicly reported data compromises decreased, but the number of data breaches with no actionable information about the root cause of the compromise grew.






































Let's personalize your content