What You Need to Know About the Psychology Behind Cyber Resilience
Dark Reading
AUGUST 25, 2022
Understanding how and why people respond to cyber threats is key to building cyber-workforce resilience.

Dark Reading
AUGUST 25, 2022
Understanding how and why people respond to cyber threats is key to building cyber-workforce resilience.

Data Breach Today
AUGUST 25, 2022
Retailer Accused of Selling Customer Data While Failing to Honor Opt-Out Requests Retailer Sephora has been fined $1.2 million as part of a settlement agreement with California's attorney general, over accusations that it violated the California Consumer Privacy Act by failing to disclose that it was selling customers' data and not honoring their opt-out requests.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
AUGUST 25, 2022
Here’s a phishing campaign that uses a man-in-the-middle attack to defeat multi-factor authentication: Microsoft observed a campaign that inserted an attacker-controlled proxy site between the account users and the work server they attempted to log into. When the user entered a password into the proxy site, the proxy site sent it to the real server and then relayed the real server’s response back to the user.

Data Breach Today
AUGUST 25, 2022
Extortion, Ransomware Groups Targeting and Harassing Entities Globally As the latest wave of ransomware attacks, extortion attempts and related fallout continues to hit hospitals globally, U.S. federal authorities have issued a new warning to the healthcare sector about Karakurt, the group behind one of the recent incidents.

Advertisement
Many organizations today are unlocking the power of their data by using graph databases to feed downstream analytics, enahance visualizations, and more. Yet, when different graph nodes represent the same entity, graphs get messy. Watch this essential video with Senzing CEO Jeff Jonas on how adding entity resolution to a graph database condenses network graphs to improve analytics and save your analysts time.

eSecurity Planet
AUGUST 25, 2022
The widely-used DevOps platform GitLab has released critical security updates for its Community Edition (CE) and Enterprise Edition (EE). The vulnerability was reported for a number of versions of GitLab CE/EE: all versions starting from 11.3.4 before 15.1.5 all versions starting from 15.2 before 15.2.3 all versions starting from 15.3 before 15.3.1.
Information Management Today brings together the best content for information management professionals from the widest variety of industry thought leaders.
Security Affairs
AUGUST 25, 2022
Russia-linked APT group Nobelium is behind a new sophisticated post-exploitation malware tracked by Microsoft as MagicWeb. Microsoft security researchers discovered a post-compromise malware, tracked as MagicWeb, which is used by the Russia-linked NOBELIUM APT group to maintain persistent access to compromised environments. The NOBELIUM APT ( APT29 , Cozy Bear , and The Dukes) is the threat actor that conducted the supply chain attack against SolarWinds, which involved multiple families of impla

Data Breach Today
AUGUST 25, 2022
The latest edition of the ISMG Security Report discusses how ransomware-as-a-service groups are shifting their business models, how investigators battling cybercrime have been hindered by GDPR, and how employees consider workplace "choice" a key factor for job satisfaction.

KnowBe4
AUGUST 25, 2022
Scammers created a deepfake video of Patrick Hillmann, Chief Communications Officer at cryptocurrency exchange Binance, in order to scam people. Hillmann explained in a blog post that he became aware of the scam after receiving messages from people he had never met, thanking him for meeting with them over Zoom.
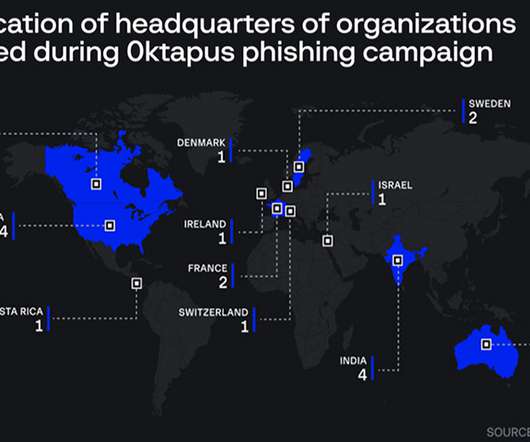
Data Breach Today
AUGUST 25, 2022
'Subject X' Suspected in Theft of Nearly 10,000 credentials at 130 Organizations An ongoing phishing campaign has compromised Cisco, Twilio and about 130 other organizations by using a lookalike Okta login page to trick employees into divulging their password and multi-factor authentication code. Researchers have traced the attacks to a 22-year-old suspect in North Carolina.

Speaker: Aarushi Kansal, AI Leader & Author and Tony Karrer, Founder & CTO at Aggregage
Software leaders who are building applications based on Large Language Models (LLMs) often find it a challenge to achieve reliability. It’s no surprise given the non-deterministic nature of LLMs. To effectively create reliable LLM-based (often with RAG) applications, extensive testing and evaluation processes are crucial. This often ends up involving meticulous adjustments to prompts.

KnowBe4
AUGUST 25, 2022
Companies heavily reliant on operational technology (OT) to function are just as much a target as businesses relying in traditional IT and are facing some of the same challenges to stop attacks.

Data Breach Today
AUGUST 25, 2022
BIN Attack, Not Data Breach, Likely Culprit Behind Spike in Fradulent Charges Cyber criminals are running scripting attacks on e-commerce sites that attempt to complete small payments by automatically inputting payment card numbers based on the Ally Bank identification number. There are no indications of a data breach at Ally Bank, says a source close to the fraud detection.

KnowBe4
AUGUST 25, 2022
If you've been approached by recruiters on LinkedIn for a potential job opportunity, you may want to pay attention to this recent scam.

Hunton Privacy
AUGUST 25, 2022
On August 24, 2022, California Attorney General Rob Bonta announced the Office of the Attorney General’s (“OAG’s”) first settlement of a California Consumer Privacy Act (“CCPA”) enforcement action, against Sephora, Inc. The OAG’s enforcement action against Sephora, which was part of a broader “enforcement sweep” of over 100 online retailers, involved allegations that Sephora failed to: Disclose to consumers that the company “sells” personal information (as broadly defined under the CCPA); Provid

Advertisement
Geopolitical risk is now at the top of the agenda for CEOs. But tracking it can be difficult. The world is more interconnected than ever, whether in terms of economics and supply chains or technology and communication. Geopolitically, however, it is becoming increasingly fragmented – threatening the operations, financial well-being, and security of globally connected companies.

Dark Reading
AUGUST 25, 2022
The Forte Group, which gained momentum as an informal organization during the pandemic, will offer career development and advocacy for women execs in cybersecurity as well as newcomers.

Threatpost
AUGUST 25, 2022
Tens of thousands of cameras have failed to patch a critical, 11-month-old CVE, leaving thousands of organizations exposed.

IT Governance
AUGUST 25, 2022
Lloyd’s of London has announced that its insurance policies will no longer cover losses resulting from certain nation-state cyber attacks or acts of war. In a memo sent to the organisation’s insurance syndicates , Underwriting Director Tony Chaudhry said that Lloyd’s remains “strongly supportive” of policies that cover cyber attacks. However, as these threats become more widespread, policies could “expose the market to systemic risks that syndicates could struggle to manage”.

Dark Reading
AUGUST 25, 2022
The "0ktapus" cyberattackers set up a well-planned spear-phishing effort that affected at least 130 orgs beyond Twilio and Cloudflare, including Digital Ocean and Mailchimp.

Advertisement
Apache Cassandra is an open-source distributed database that boasts an architecture that delivers high scalability, near 100% availability, and powerful read-and-write performance required for many data-heavy use cases. However, many developers and administrators who are new to this NoSQL database often encounter several challenges that can impact its performance.

Jamf
AUGUST 25, 2022
With Apple School Manager introducing federated authentication with Google Workspace, it is now easier than ever for educators to work with the Apple and Google ecosystems side by side, getting the most out of each. Read on for observations about the power of Google apps on iPad.

KnowBe4
AUGUST 25, 2022
First debuted in July 2021, this ransomware gang that engages in their own attacks and offers a RWaaS model, has come back into the limelight offering victims several extortion payment options.

Dark Reading
AUGUST 25, 2022
The US Cybersecurity and Infrastructure Security Agency had wanted federal agencies to implement the fix for the RCE flaw in Hikvision cameras by Jan. 24, 2022.

KnowBe4
AUGUST 25, 2022
Despite the crypto market’s loss of over $1 trillion in value since the beginning of the year, the value of the digital currency isn’t what makes it a popular choice for cybercriminals.

Advertisement
“Reimagined: Building Products with Generative AI” is an extensive guide for integrating generative AI into product strategy and careers featuring over 150 real-world examples, 30 case studies, and 20+ frameworks, and endorsed by over 20 leading AI and product executives, inventors, entrepreneurs, and researchers.
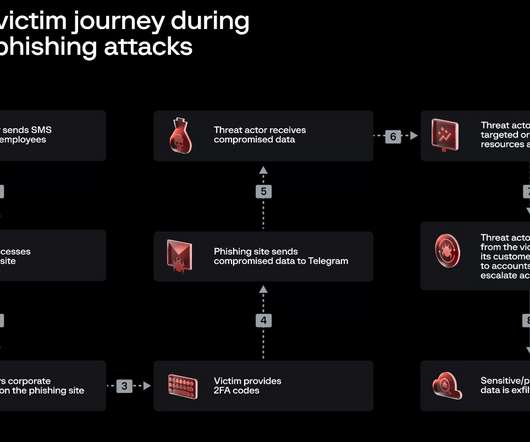
Security Affairs
AUGUST 25, 2022
The threat actors behind Twilio and Cloudflare attacks have been linked to a phishing campaign that targeted other 136 organizations. The threat actors behind the attacks on Twilio and Cloudflare have been linked to a large-scale phishing campaign that targeted 136 organizations, security firm Group-IB reported. Most of the victims are organizations providing IT, software development, and cloud services.

KnowBe4
AUGUST 25, 2022
As cyber insurers evolve their understanding of the cyber attack landscape, who’s responsible, and what’s at stake, a logical next step is taken by Lloyd’s to better isolate what is covered and what isn’t.

Dark Reading
AUGUST 25, 2022
The FTK 7.6 portfolio promises better integration with other security and network resources, as well as unified analysis of mobile and computer evidence.

WIRED Threat Level
AUGUST 25, 2022
An Ohio judge ruled that such surveillance to prevent cheating could form a slippery slope to more illegal searches.

Advertisement
If you’re considering migrating from DataStax Enterprise (DSE) to open source Apache Cassandra®, our comprehensive guide is tailored for architects, engineers, and IT directors. Whether you’re motivated by cost savings, avoiding vendor lock-in, or embracing the vibrant open-source community, Apache Cassandra offers robust value. Transition seamlessly to Instaclustr Managed Cassandra with our expert insights, ensuring zero downtime during migration.

Dark Reading
AUGUST 25, 2022
Online Security autonomously blocks malicious URLs, extensions, ad trackers, and pop-ups 24/7, protecting consumers from complex and rapidly evolving cyber threats online.

OpenText Information Management
AUGUST 25, 2022
IT, info-security, compliance, HR and business unit leaders are increasingly tasked with collaborating with their legal department colleagues to mitigate legal risk to the organization, whether promulgated by litigation, regulatory investigations, or suspicions of internal wrongdoing such as IP theft, cybersecurity breaches and data privacy compliance.

Dark Reading
AUGUST 25, 2022
Optiv's Black Employee Network offers the scholarship, paid out over 4 years, for students seeking a career in the cybersecurity/information security industry.
Let's personalize your content