Phishing Attack Used Spoofed COVID-19 Vaccination Forms
Data Breach Today
AUGUST 30, 2021
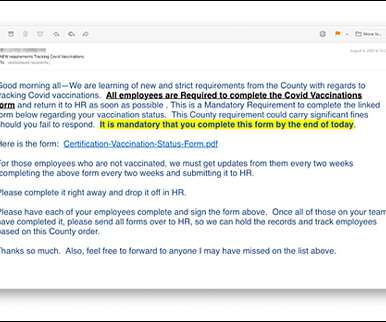
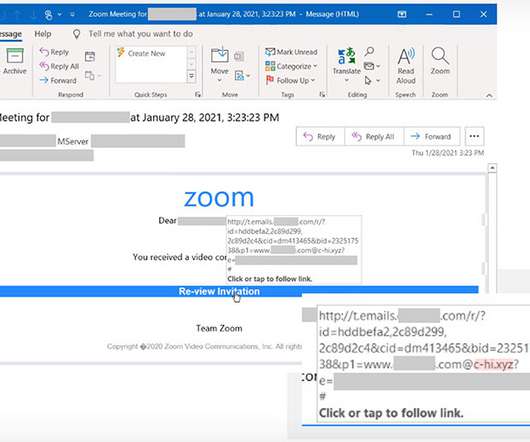
Researchers Find Fraudsters Pose as HR Execs to Harvest Credentials A recently uncovered phishing campaign used fake COVID-19 vaccination forms - and took advantage of confusion over whether employees will return to their offices this fall - to harvest workers' email credentials, according to analysts with security firm INKY. The malicious messages appear to come from victims' HR departments.


































Let's personalize your content