Hades Ransomware Targets 3 US Companies
Data Breach Today
MARCH 25, 2021
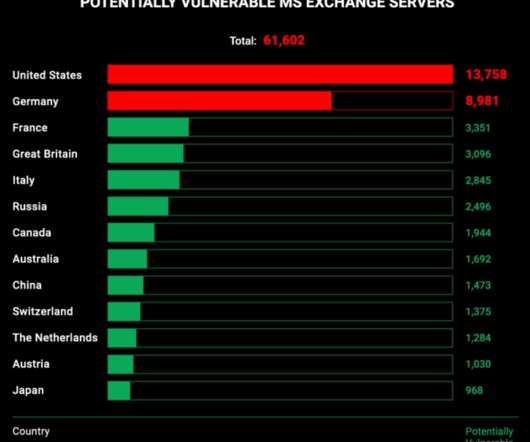
Accenture Describes Highly Targeted Campaign A previously unknown threat group is deploying Hades ransomware as part of an ongoing campaign that has already targeted three U.S. companies, Accenture's cyberthreat intelligence group reports.







































Let's personalize your content