5 Critical Questions Raised by Water Treatment Facility Hack
Data Breach Today
FEBRUARY 9, 2021
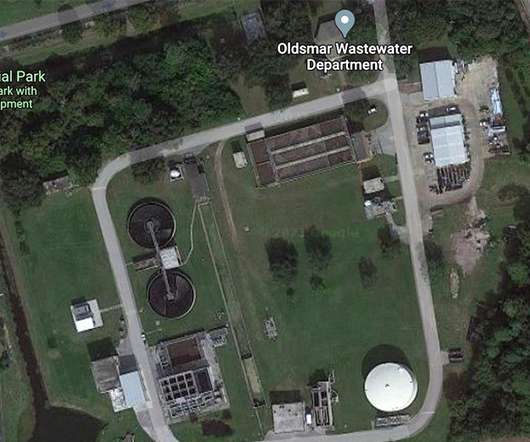
Incident Highlights the Need to Enhance OT Security As the investigation into the hacking of a water treatment facility in Florida continues, cybersecurity experts say the incident points to the urgent need to enhance operational technology security. Here are five key questions the incident raises.






































Let's personalize your content