Cybercriminal Service ‘EvilProxy’ Seeks to Hijack Accounts
Data Breach Today
SEPTEMBER 5, 2022
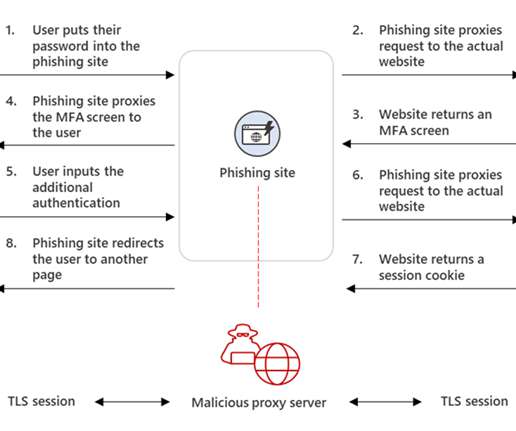
EvilProxy Bypasses MFA By Capturing Session Cookies One of the biggest challenges for cybercriminals is how to defeat multifactor authentication. New research has uncovered a criminal service called “EvilProxy” that steals session cookies to bypass MFA and compromise accounts.

















Let's personalize your content