Gamaredon group uses a new Outlook tool to spread malware
Security Affairs
JUNE 12, 2020
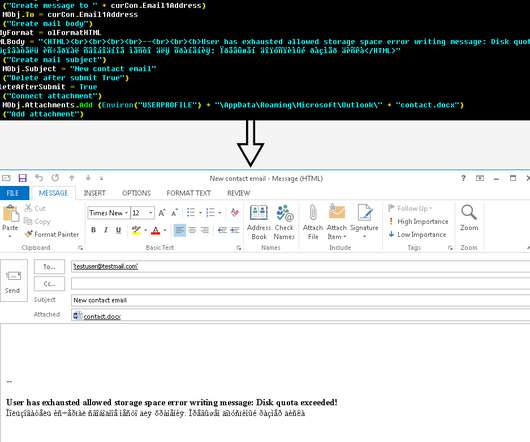
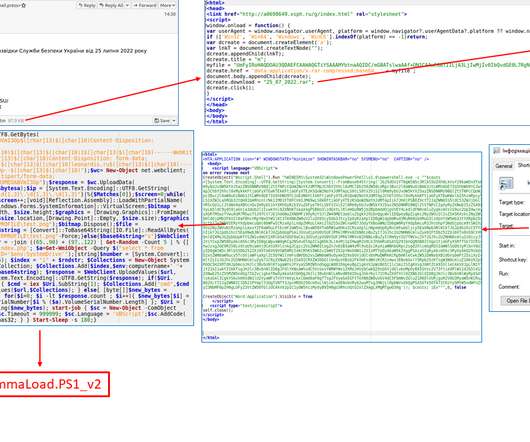
Russia-linked Gamaredon APT use a new module for Microsoft Outlook that creates custom emails with malicious documents and sends them to a victim’s contacts. The group targeted government and military organizations in Ukraine. The VBA code builds the email body and attaches the malicious document to the email in both .docx








































Let's personalize your content