Calculating electronic records storage costs
The Schedule
APRIL 14, 2020
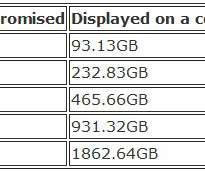
If your organization tends to retain records for the long-term or is not in the habit of purging routine, obsolete, and trivial data, this number will tend to grow exponentially. Be aware: the cost may differ depending on whether you wish to store sensitive or non-sensitive data. put, copy, list, select) and data retrieval.















Let's personalize your content